Virtual private networks are far from one-size-fits-all services. Depending on the use case, there are different configurations for connections, different encryption protocols to use, and, of course, different outcomes when it comes to user experience.
Today, our digital privacy experts are diving into the world of enterprise-level security. Specifically, we’re diving into the powerful devices that keep thousands of remote workers securely connected to their company networks. We’re talking about VPN concentrators, the unsung heroes of corporate cybersecurity.
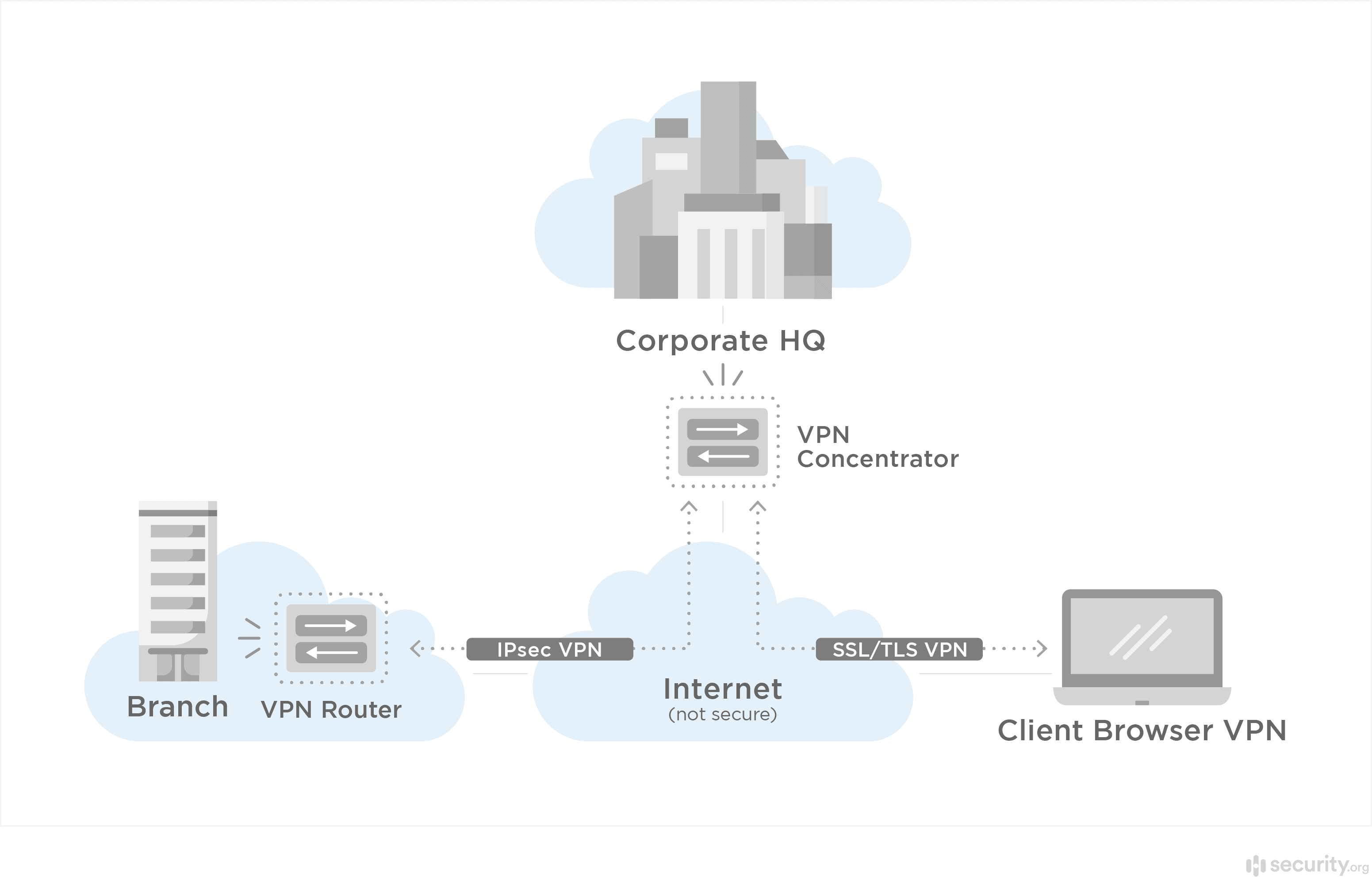
What Is a VPN Concentrator?
Think of a VPN concentrator as the Swiss Army knife of enterprise network security. It’s a dedicated hardware device (sometimes virtual) that manages hundreds or thousands of simultaneous VPN connections from a central location. Unlike your high-quality personal VPN that protects just your devices, a VPN concentrator is built to support entire remote workforces.
What Does a VPN Concentrator Do?
A VPN concentrator establishes multiple encrypted VPN tunnels at the same time, providing secure connections for multiple VPN nodes. A server-side feature, a VPN concentrator extends a VPN router to thousands of users, giving them encrypted tunnels so they can access a centralized system. Additionally, a VPN concentrator authenticates users, encrypts and decrypts their data, and changes their IP addresses for maximum digital security.1
How Does a VPN Concentrator Work?
Your company’s VPN concentrator creates individual encrypted tunnels for each connected remote worker. That ensures employee traffic is encrypted before it reaches the internal network, keeping their connection secure. The concentrator handles all the heavy lifting: authenticating users, managing encryption keys, and routing traffic securely between remote devices and your internal network resources.
The Most Common VPN Concentrator Options
Unless you’re in the IT department of a large enterprise, you probably don’t have to worry about shopping for a VPN concentrator. That being said, here are the most popular VPN concentrators today:
- Cisco Meraki MX Series
- Fortinet FortiGate
- Palo Alto Networks GlobalProtect
Who Uses VPN Concentrators?
VPN concentrators are the go-to solution for Fortune 500 companies, government agencies, healthcare systems, and educational institutions. Basically any organization with hundreds or thousands of remote users enables secure remote work with VPN concentrators.
The thing about VPN concentrators is that they’re expensive, so they make sense for large businesses only. For small businesses, it’s best to use a VPN router or VPNs on devices directly. Learn more about the best VPNs for business.
FYI: Typically, only large enterprises use VPN concentrators. Small businesses should look for VPN clients instead.
When Do You Need a VPN Concentrator?
Here’s the litmus test. If your organization has more than 100 remote users who need simultaneous access to internal resources, a VPN concentrator makes financial and operational sense. Below that threshold, you’re better off with business VPN services or router-based solutions that cost a fraction of the price.
VPN Concentrator Alternatives
As we mentioned earlier, VPN concentrators aren’t the only game in town. Let’s compare them to some other VPN options.
VPN Concentrator vs. VPN Router
Using a VPN on your router will encrypt all of the devices connected to that router; i.e., all of the devices on your network. However, a router VPN won’t help you access a centralized network, so it doesn’t have the same function as a VPN concentrator.

Pro Tip: We recommend using router VPNs either at home or in a physical office.
VPN Concentrator vs. Site-to-Site VPN
For businesses juggling multiple office locations, site-to-site VPNs create permanent encrypted connections between your different branches. Think of it as building secure bridges between your offices. By contrast, a VPN concentrator is like having a secure gate that remote workers pass through to reach headquarters.
VPN Concentrator vs. IPsec Encryption
IPsec is a protocol that protects data as it travels in the tunnel. It authenticates IP packets via RSA encrypted nonces, digital certificates, or pre-shared keys.2 IPsec occurs in the network layer, while VPN concentrators are server-side. However, these options aren’t mutually exclusive; rather, some VPN concentrators use IPsec protocols for data confidentiality, integrity, and authentication.
VPN Concentrator vs. VPN Client
A VPN client is the software that connects a user and a VPN server. While some VPN clients work in the background, some have front-end interfaces and require action from the user. And while some VPN clients are installed on computers as applications, some offices have hardware devices pre-installed with VPN software.
While a VPN client handles one user at a time, a VPN concentrator juggles thousands simultaneously. It’s like comparing a personal taxi to a massive transit hub. Both get you where you need to go, but they operate on completely different scales.
VPN Concentrator Encryption Protocol Types
If your workplace uses a VPN concentrator, chances are that you’re using one of the following types of encryption:
- PPTP/MPPE: Multi-protocol VPNs use Microsoft Point-to-Point Encryption, as PPTP on its own doesn’t provide data encryption.
- L2TP/IPsec: Also called L2TP over IPsec, the Layer 2 Tunneling Protocol is used most often for remote-access VPNs with Windows 2000 operating systems as well as dial-in users. IPsec handles the encryption.3
- IPsec: Hello, old friend. IPsec provides strong encryption and authentication in one of two modes, detailed below.
VPN Concentrator Transport Mode
Here’s a quick breakdown. Tunnel mode wraps your entire data packet in encryption (like putting a letter in a locked box). Transport mode only encrypts the contents (like writing in code but leaving the envelope visible). For IPsec VPN concentrators, transport mode remains the default choice for efficiency.4
SSL vs. IPsec
SSL, which stands for Secure Sockets Layer, uses a handshake method to authenticate sessions and establish secure connections, more secure than IPsec. SSL is more compatible with firewalls and doesn’t support compression. IPsec, on the other hand, is better for dial-up or low-bandwidth networks as well as wireless networks. But don’t worry; if you’re an employee who has to use a VPN concentrator, you probably won’t have to dive deep into its internet protocols.
| Function | IPsec | SSL |
|---|---|---|
| Client authentication | Must | Option |
| Compression support | Yes | OpenSSL only |
| Configuration | Difficult | Easy |
| Handshake time | Slow | Fast |
| Interoperability problem | Yes | No |
| Pre-shared key | Yes | No |
| TCP application support | All | Some |
| Throughput rate | High | High |
| UDP support | Yes | Yes (with DTLS) |
VPN Concentrator Impact on Performance
Let’s be real. Connecting through a VPN concentrator isn’t always smooth sailing. It can cause performance issues such as:
- Latency increases of 10 to 30ms on average, which could affect real-time applications like video conferencing
- Limited support for certain mobile apps that require direct connections
- May lose internet connection
- Slow page loading
- Faulty connections
If you’re having any of the above issues with a VPN concentrator, try switching to another server, and if that doesn’t work, contact your company’s IT department.
VPN Concentrator Pros and Cons
Let’s break down what we like and don’t like about VPN concentrators.
Pros
- Great for connecting a high number of remote employees to a centralized network
- Quickly generates hundreds to thousands of tunnels in less time than connecting individual VPN clients
- Centralizes security management and access control
- Supports advanced authentication methods including multi-factor authentication
Cons
- Can have deployment issues at times
- Expensive to implement
- Not good for smaller companies or home networks
- Requires dedicated IT expertise for maintenance and troubleshooting
What Is a VPN?
Getting back to basics, a VPN is a virtual private network. VPNs hide your browsing activity; also, VPNs encrypt your IP address, hiding your real IP address from your internet service provider (ISP). Learn everything there is known about VPNs in our VPN how-to hub.
Recap
VPN concentrators remain the backbone of enterprise remote access. They’ve only grown in importance as hybrid work continues to dominate the corporate landscape. While they’re overkill for personal use or small businesses, these powerful devices keep millions of remote workers securely connected to their company networks every day.
Frequently Asked Questions
After being inundated with questions about VPN concentrators, we’ve answered the most common ones below.
-
Do I need a VPN concentrator?
If you run a large enterprise with hundreds or thousands of remote employees who need to access a centralized network, then yes, you need a VPN concentrator. However, if you’re part of a small and/or in-person business, then you don’t need a VPN concentrator.
-
Where should a VPN concentrator be installed?
A VPN concentrator should be installed at your network perimeter, typically in your DMZ (demilitarized zone) or directly behind your firewall. This positioning allows it to authenticate and encrypt traffic before it enters your internal network.
-
What does a Cisco VPN concentrator do?
A Cisco VPN concentrator connects remote employees to a centralized network, encrypting their web activity and IP addresses in tunnels along the way.
-
How much does a VPN concentrator cost?
Entry-level VPN concentrators for small enterprises start around $200, while high-capacity models for large corporations can exceed thousands. Most mid-sized businesses spend between $800 and $1,500 for a concentrator that handles 500 to 1,000 concurrent users.