Connecting to a VPN hides your IP address – or at least that’s how it should work. But did you know there’s a browser feature that can leak your IP address while you’re protected by a VPN? What’s worse, that feature is default to most browsers.
We’re talking about WebRTC, and in this guide, we’ll tell you all about it. We’ll discuss what WebRTC is and what it does, how WebRTC leaks happen, and most importantly, how you can stay safe.
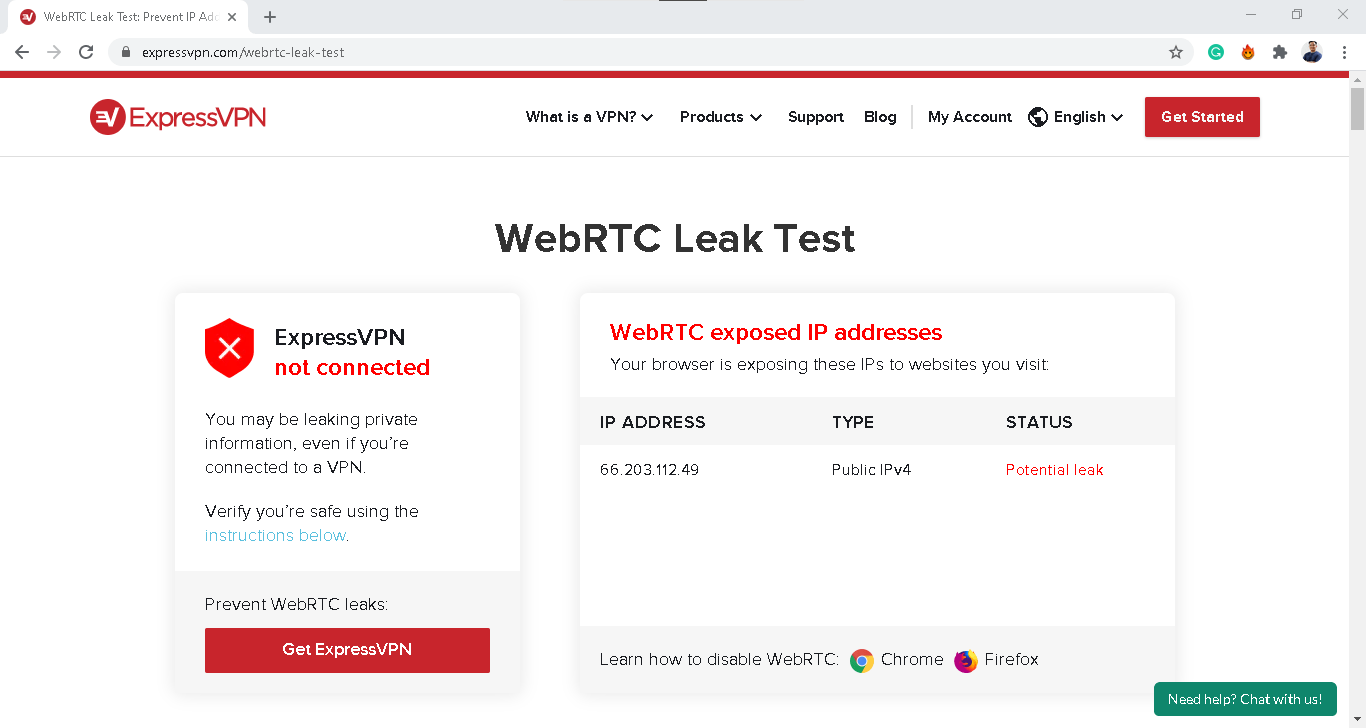
WebRTC Leaks
To put it simply, a WebRTC leak can reveal your public IP address to an attacker. Your public IP address is your address on the internet – think of it as your device’s phone number or home address. It’s how the internet knows where to send data so you can download files, view webpages, communicate with others, and so on.
WebRTC revealing your IP address isn’t problematic by itself. There’s a lot of things you do on a daily basis that involves your public IP address, such as visiting a website. However, it becomes a major problem if you’re using a VPN.
One of the main reasons our experts recommend using a VPN is to hide your real IP address. It gives you a private IP address so you can do things like change your Netflix region and keep yourself anonymous while visiting a website. However, if WebRTC is leaking your IP address, it might be possible for others to still see your real IP address.
The result? Well, there are many things others can do with your IP address. For example:
- Your internet service provider can track your online activity.
- Governments can spy on you.
- Cybercriminals can access or steal personal data.
- Advertisers can send you personalized spam.
Know the Difference: Two or more devices can have the same private (local) IP address, but public (real) IP addresses are unique. That’s why concealing your public IP address is key to achieving online privacy.
What Is WebRTC?
WebRTC poses big security risks to VPN users, but why does WebRTC still exist? Because it’s a useful feature. WebRTC stands for Web Real-Time Communication. It’s a free and open-source project that provides web browsers and mobile apps with real-time communication capabilities.1
One of the features of WebRTC is that it allows direct communication between browsers or apps without an intermediate server. That translates to faster and less laggy transfers of video, audio, and large files, which is why WebRTC is popular among video chat, livestreaming, and file transfer services. Some of the apps that use WebRTC are:
- Google Meet and Google Hangouts
- Facebook Messenger
- Discord
- Amazon Chime
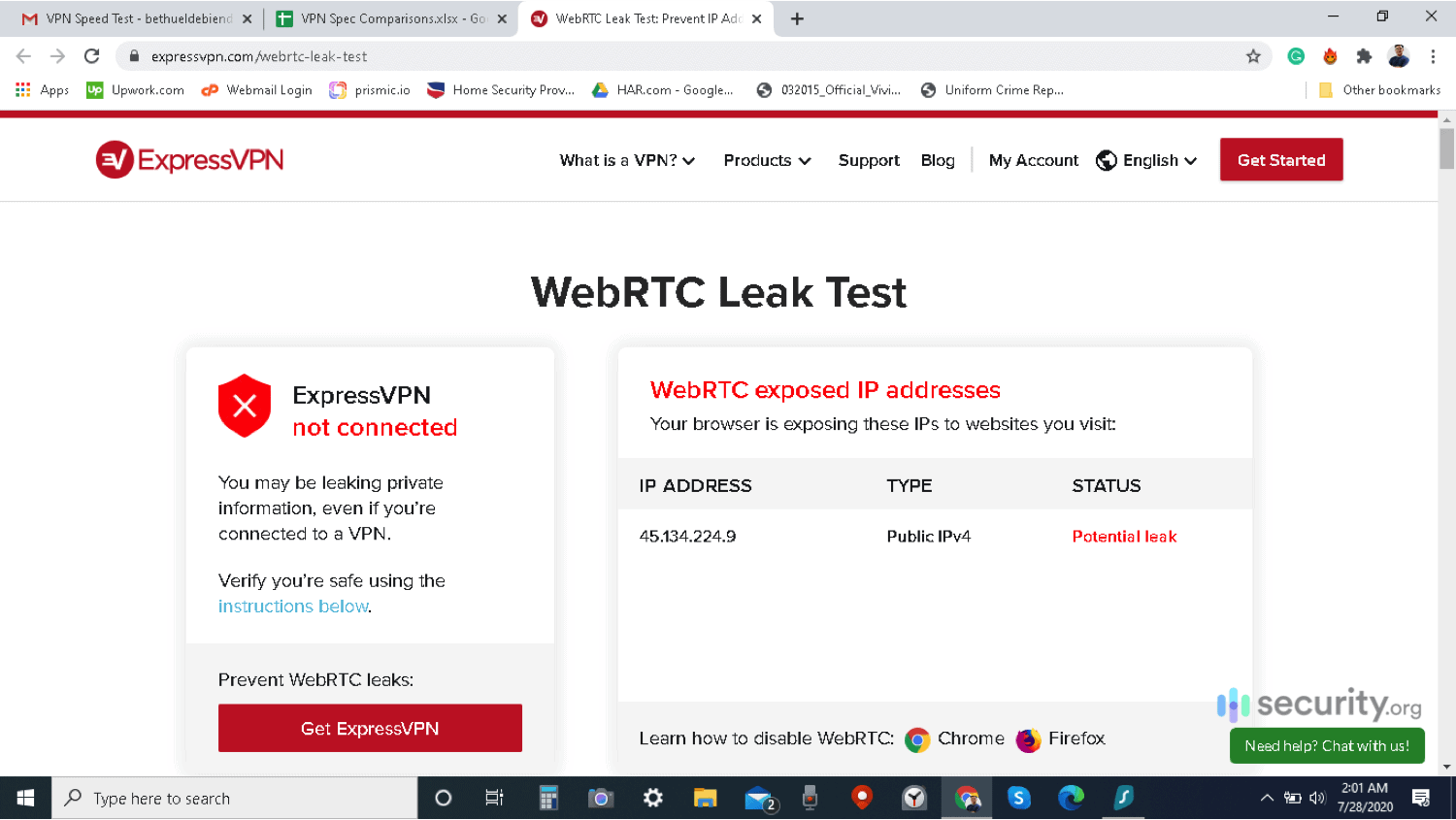
The Problem With WebRTC
WebRTC is a useful feature, but as we said earlier, it becomes a problem if you’re trying to hide your IP address. That’s due to how WebRTC works. In order to establish a communication line between two devices, those two devices must know each other’s IP address. That function is what attackers exploit.
This is where WebRTC leaks come in. Third-party actors can exploit WebRTC communication channels to obtain the real IP addresses of the parties involved, which would be a privacy threat. WebRTC leaks can even bypass the encrypted tunnels of some VPNs.
To make matters even worse, the exchange of IP addresses between two devices is a part of WebRTC’s basic functionality; it’s not something you can disable or skip. So how can we protect ourselves from WebRTC leaks? There are two options:
- Find and block WebRTC leaks
- Disable WebRTC on your browser entirely
Of course, just because your browser uses WebRTC doesn’t mean you’re vulnerable. Some VPNs tune their services to prevent WebRTC leaks from happening. We test several dozen VPNs, and among them, we’ve found only a small percentage that can’t block WebRTC leaks. Still, it pays to be vigilant, especially with your privacy on the line. So here’s how you can check for a WebRTC leak and prevent it from happening to you in the future.
Note: Firefox, Google Chrome, Opera, and Microsoft Edge are most vulnerable to WebRTC leaks because these browsers default to WebRTC.
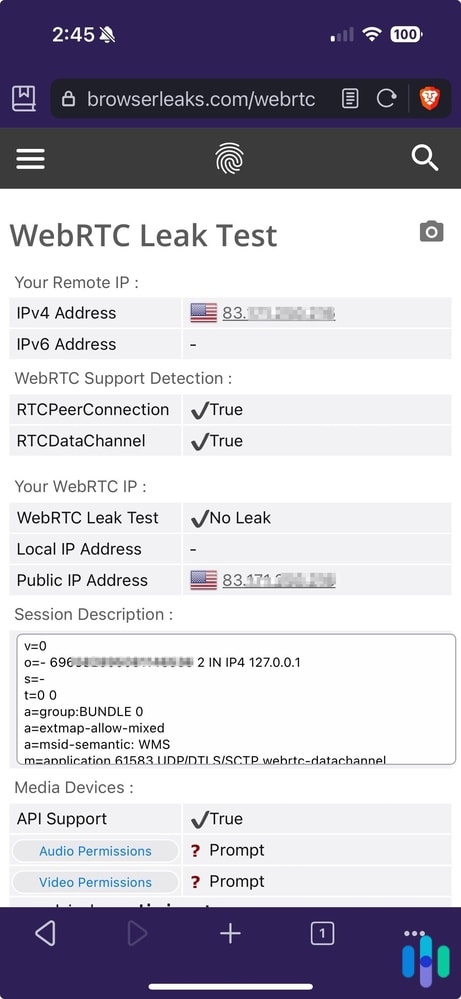
How to Check for WebRTC Leaks
It’s pretty easy to check your browsers for WebRTC leaks.
- First, find out and write down your device’s public IP address. If you need instructions on finding your IP address, check out these how-to guides:
- Next, use the WebRTC leak test tool on ExpressVPN’s website.2
- If the IP address on the leak test tool matches your device’s IP address, then your browser might be leaking your IP address via WebRTC.
Remember that WebRTC is a browser feature, so if you use different browsers, be sure to test them all.
How to Block WebRTC Leaks
Now, if your browser is leaking your IP address via WebRTC, you need to block the leak immediately. You can do that by using VPNs. Yes, we know, we said earlier that WebRTC leaks can bypass some VPNs, but only because not all VPNs pay attention to this type of leak.
That’s why, when we’re testing VPNs, we always perform WebRTC leak tests on them. For example, all the best VPNs in our book passed the WebRTC leak test. That means they allow WebRTC to function, but only through their encrypted tunnels. That way, outsiders and third parties can’t exploit WebRTC communication channels to obtain IP addresses.
To check if your VPN is capable of blocking WebRTC leaks, here’s what you should do.
How to Block WebRTC Leaks with a VPN
- Disable your VPN.
- Find and note your device's public IP address.
- Turn your VPN back on.
- Open your browser to ExpressVPN's WebRTC leak test tool.
- If it's showing your device's real IP address from step two, then there is a leak. If it's showing a different IP address, then your VPN works.
If you find out that your VPN isn’t doing anything to prevent WebRTC leaks, you can contact your VPN provider and cancel your VPN service, switch to a new VPN, or proceed to the most surefire solution for WebRTC leaks: disabling WebRTC altogether.
Pro Tip: WebRTC leaks are one of the things we check when testing VPNs. Learn more about how we choose VPNs in our VPN guide.
How to Disable WebRTC
Disabling WebRTC should be a last resort. If you can, we suggest switching VPN providers to one that can block WebRTC leaks. That way, you still enjoy the benefits of WebRTC without the risks. In case that’s not possible, though, disabling WebRTC altogether is also a solution – a surefire one. The catch is you won’t be able to use services that require WebRTC.
Here’s how you can disable WebRTC on Chrome, Firefox, and Edge. And keep in mind, you have to disable WebRTC on all the browsers you use on a regular basis.
Chrome
Fun fact: Google is one of the major supporters of the WebRTC project, and as such, there is no way to disable WebRTC on Chrome permanently. That’s unfortunate; however, there are browser extensions that will let you manage or disable WebRTC temporarily.
- WebRTC Network Limiter: This Google-made add-on doesn’t turn off WebRTC, but it reconfigures WebRTC’s traffic routing options. One of the things it does is that it requires WebRTC traffic to go through proxy servers, making it harder for anyone to steal IP addresses.3 This is similar to what the best VPNs for Chrome do, but instead of encrypted tunnels, the WebRTC Network Limiter uses proxy servers.
- WebRTC Control: This simple browser extension lets you turn WebRTC on and off. When WebRTC Control is on, your Chrome browser will stop using WebRTC.
- WebRTC Leak Prevent: Similar to the WebRTC Network Limiter, this extension prevents WebRTC leaks by controlling hidden WebRTC privacy settings and routing options.
- WebRTC Protect – Protect IP Leak: By default, this browser extension disables WebRTC. However, you can configure it to let you keep using WebRTC. If you do, it will control your WebRTC routing options, kind of like WebRTC Network Limiter.
Firefox
Like Google, Mozilla Firefox is a heavy supporter of WebRTC. If VPNs for Firefox can’t prevent WebRTC leaks, you can turn off WebRTC entirely by following these steps:
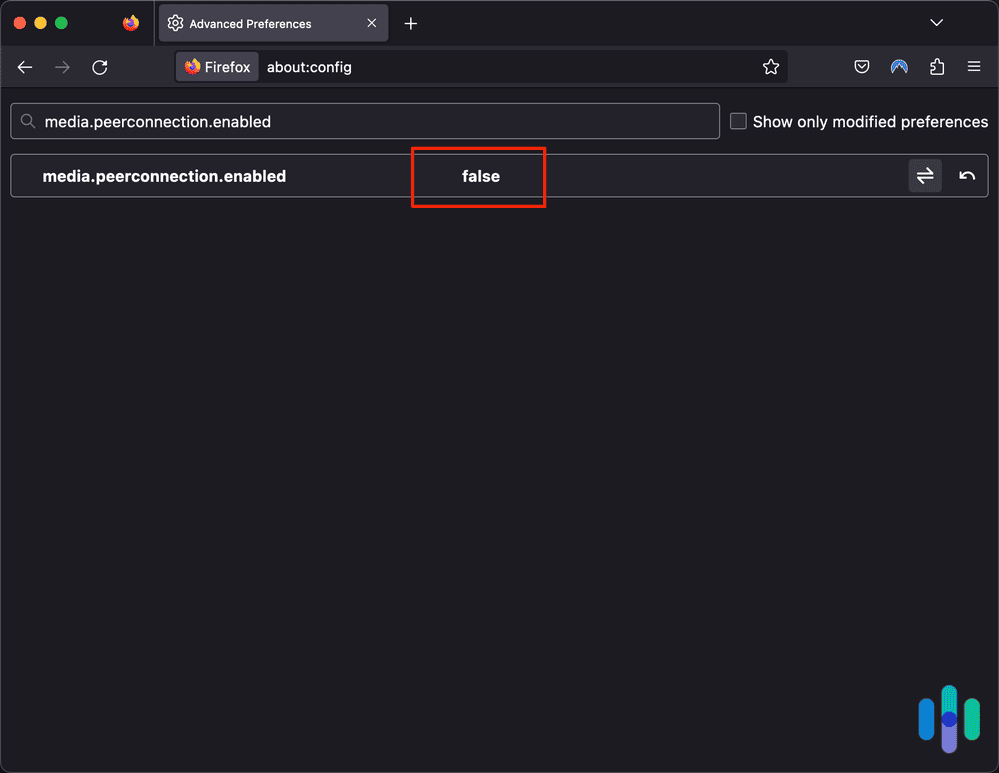
- Open Firefox.
- Type about:config into the address bar.
- Click I Accept The Risk!
- Type media.peerconnection.enabled into the search bar.
- Double-click the result to change the value from True to False.
Edge
Lastly, here’s how to disable WebRTC on Microsoft Edge:
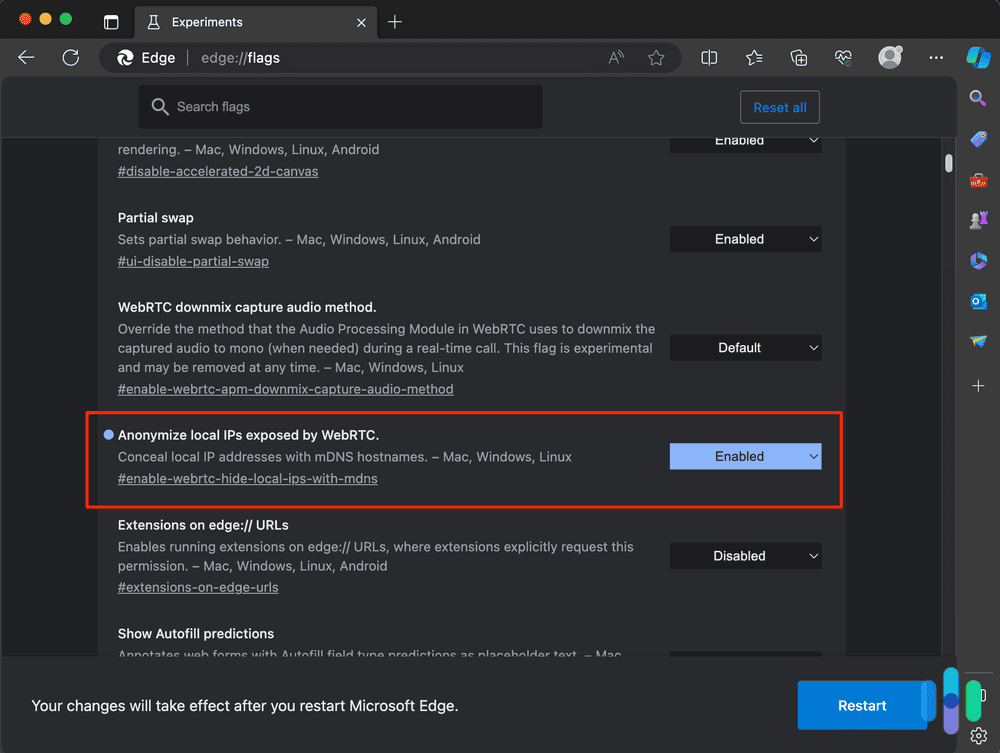
- Open Edge.
- Type edge://flags into the address bar.
- Hit Enter.
- Look for Anonymize Local IPs Exposed By WebRTC.
- Click the drop-down menu next to it and select Enable.
- Edge will prompt you to restart the browser for the new settings to take effect.
- Close and then reopen Edge.
What About Device IDs?
Although the main issue with WebRTC leaks is the leakage of IP addresses, third parties can also use WebRTC to obtain some information about the media devices on your computer. These are your microphones, cameras, audio output, CD players, and others. For example, if you go to the Browser Leaks website,4 which is another website that can detect WebRTC leaks, you can see what types of media devices are on your computer.
Fortunately, browsers don’t allow third parties to obtain device IDs, which are unique 16-digit codes specific to media devices. However, third parties can still see what types of media devices you have, as well as the hashes that your browser generates in place of device IDs.
And since these browser-generated hashes change only when you clear your browsing data, it could only be a matter of time until someone figures out a way to use that information against you. The good news is, blocking WebRTC leaks, either by using VPNs or disabling WebRTC, prevents these pieces of information from leaking.
Recap
Despite all the good things WebRTC brings — faster livestreaming, less laggy video communication, smoother file transfers — we can’t ignore the threat that its leaks pose to our privacy. As we always say, privacy is everything and we can never be too secure online. While we wait for WebRTC developers to come up with solutions for WebRTC leaks, our best bets for now are to use reliable VPNs or to disable WebRTC entirely.
FAQs
To sum everything up, let's answer some FAQs about WebRTC and WebRTC leaks.
-
How do I fix WebRTC leaks?
You can fix WebRTC leaks by either using a VPN that blocks WebRTC leaks or disabling WebRTC on your browsers entirely. The former is the best solution if you want to enjoy all the functionalities that come with WebRTC, but with better security. VPNs that block WebRTC leaks allow WebRTC to work on your browser, but only through encrypted tunnels. That prevents anyone from stealing your IP address by exploiting WebRTC communications.
-
How do I stop WebRTC from leaking in Chrome?
To stop WebRTC from leaking in Chrome, you can use a VPN whenever you use Chrome. VPNs route WebRTC communications through encrypted tunnels, preventing WebRTC leaks. You can also use Chrome extensions like WebRTC Network Limiter, which reconfigures the routing options of WebRTC to make them more secure, or WebRTC Control to turn WebRTC on and off at will.
-
Should I turn off WebRTC?
That depends. You shouldn’t turn off WebRTC on your browser if you use websites or services that rely on WebRTC, like Google Hangouts, Google Meets, or Facebook Messenger. However, if the services you use don’t use WebRTC, turning off the feature prevents WebRTC leaks entirely.
-
How do I know if WebRTC is leaking?
You can find out if WebRTC is leaking by following these simple steps:
- Find and note your device’s public IP address.
- Go to ExpressVPN’s WebRTC leak test website or any online tool that detects WebRTC leaks.
- If your public IP address matches the IP address on the website, then your WebRTC is leaking.