America's Password Habits
Bad habits die hard: Two out of three people still reuse passwords across accounts, one in three share codes with others, and nearly 40 percent have been hacked.
By now, everyone should know the importance of using strong, random, and hard-to-guess passwords. Cybersecurity experts – including ourselves – have been preaching it for the last few decades. It is, however, more important now than ever to use strong passwords, given the recent dramatic surge in Internet crime.
But has that inspired Americans to improve their digital security habits? Our research shows that while there are some behavioral improvements over last year’s results, there are still weak spots in the country’s cybersecurity practices.
The Good News:
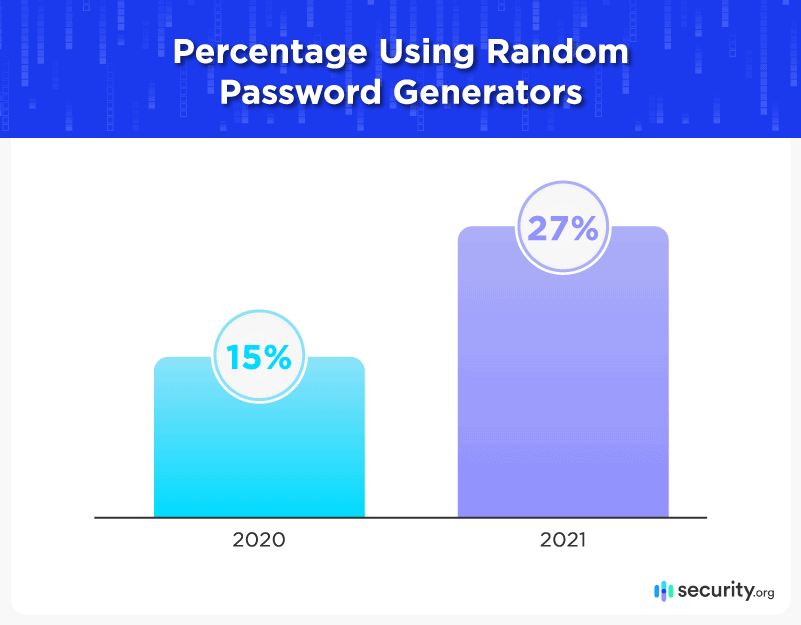
- Use of password generators nearly doubled over the previous year, from 15 percent to 27 percent.
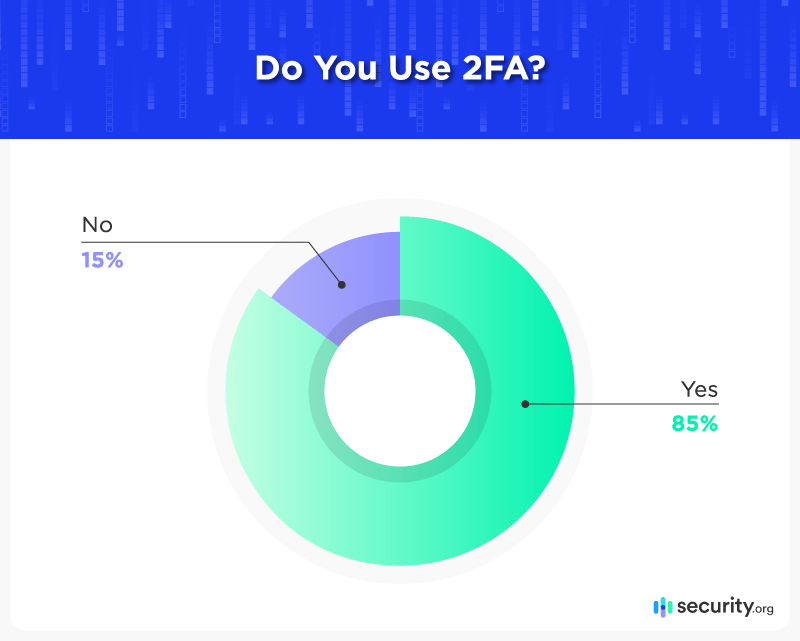
- 85 percent of respondents have employed two-factor authentication, adding an extra layer of online security.
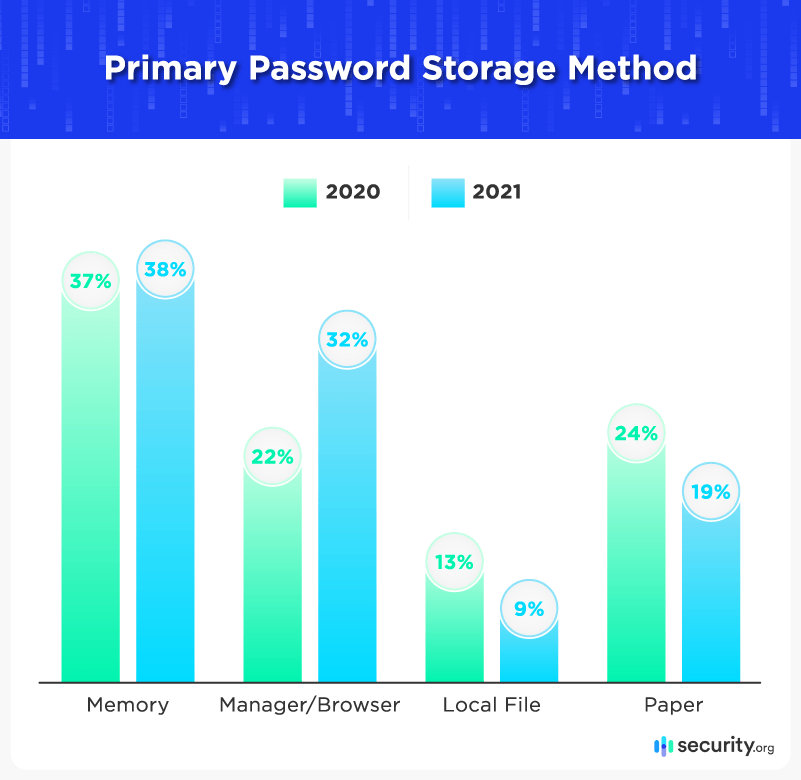
- Password vaults or managers are now more widely used, with 32 percent now reportedly using one. That’s up from 22 percent the previous year.
The Bad News:
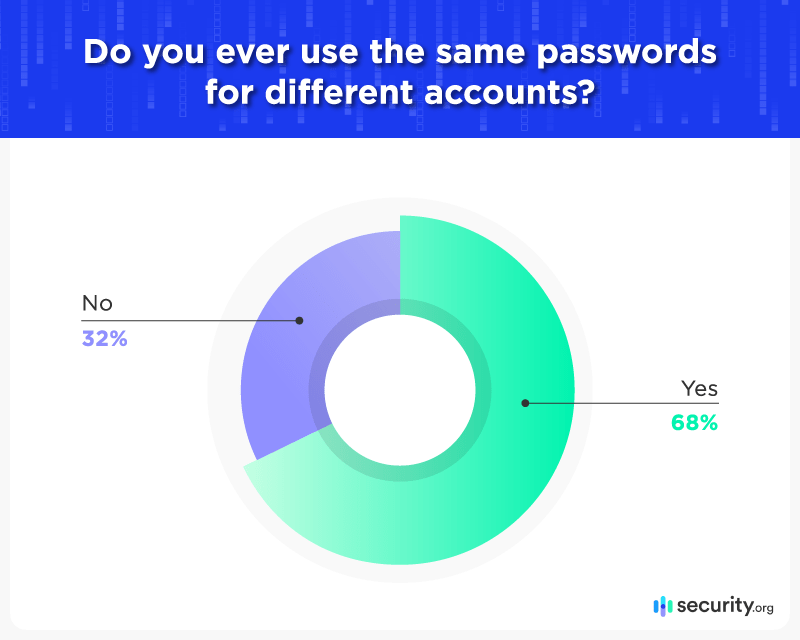
- More than two in three people continue to use the same passwords across multiple accounts;
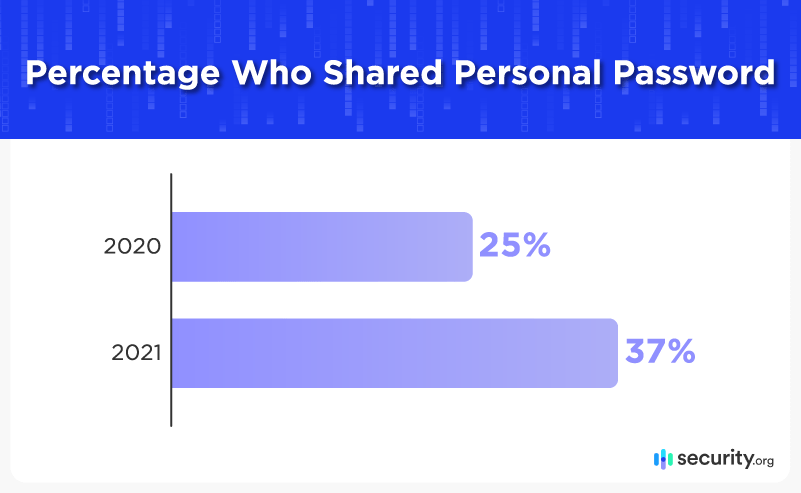
- About 37 percent are still sharing their personal passwords with other people. Alarmingly, that’s an increase from 25 percent last year.
- Less than half of people feel very confident that their passwords are secure from compromise.
Read on for a revealing analysis of Americans’ password habits, as well as a guide to the best practices to keep you safe and secure online.
Password Creation Habits
Gone are the days where hackers had to guess passwords themselves. Now, they can use software to crack seemingly uncrackable passwords. These pieces of software crunch through whole dictionaries in seconds to try to guess commonly used words as passwords. Some are sophisticated enough to use a person’s personal information like birthday, spouse’s name, kids’ birthdays, etc. That is why we recommend using a random password generator that can create randomized passwords. More on that later.
Unfortunately, we found that a majority of Americans violate the first password commandment by using the same login for more than one account – a practice that can seriously compromise your online security. If one account is hacked, all the other accounts that use the same password can potentially be hacked. It’s like having one key for all doors in your house; it may be convenient, but it makes things just as convenient for thieves when they get access to that key.
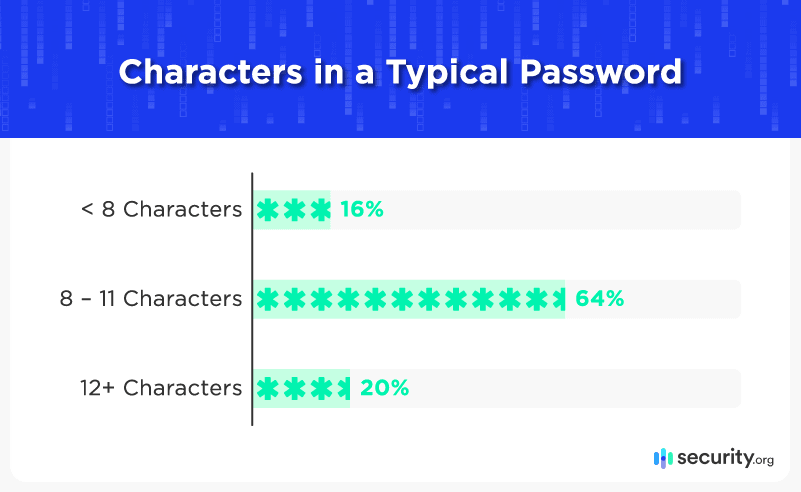
On the plus side, many people appear to have learned the dangers of shorter passwords, leading a large majority (84 percent) to use at least eight-character codes when logging in:
Of course, it’s not just the number of characters but how they’re chosen that counts most when it comes to security. Placing new punctuation into old passwords doesn’t fool an algorithm. Arranging words randomly doesn’t fluster a dictionary database. Combining your pet’s name and your birthday isn’t cryptic when that info is available on Facebook.
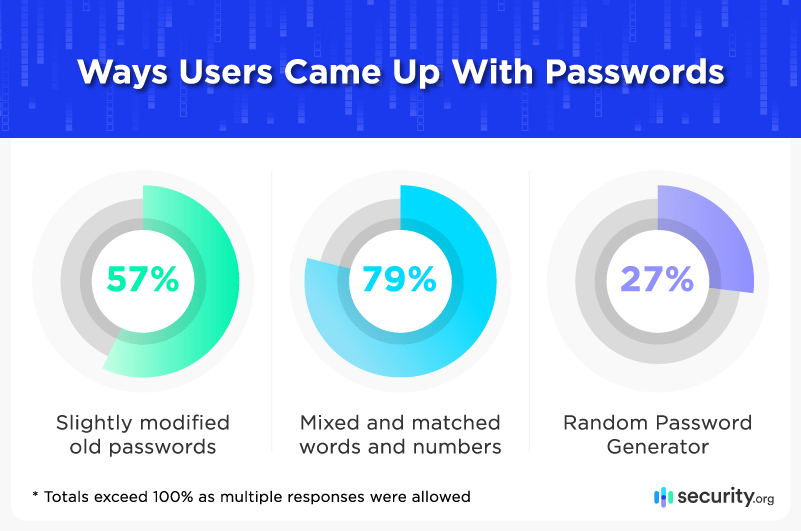
The most impenetrable passwords are constructed with randomly selected characters, but we found that many people still conjured up their codes using repetition and familiar words:
Recycled passwords are the easiest to hack, even when they’ve been slightly changed – which is how our respondents come up with most of their codes. 57 percent admitted to merely tweaking old passwords and substituting characters (like typing “@” for “a” or “1” for “i”) when updating their login information.
Slightly more secure were the 79 percent of users who generated their own passwords by creating new combinations of words and numbers. While methods varied (19 percent used full sentences, 17 percent selected randomly from the dictionary, and 13 percent claimed to roll word dice), they all shared the same flaw: real words are recognizable strings that can be more easily cracked.
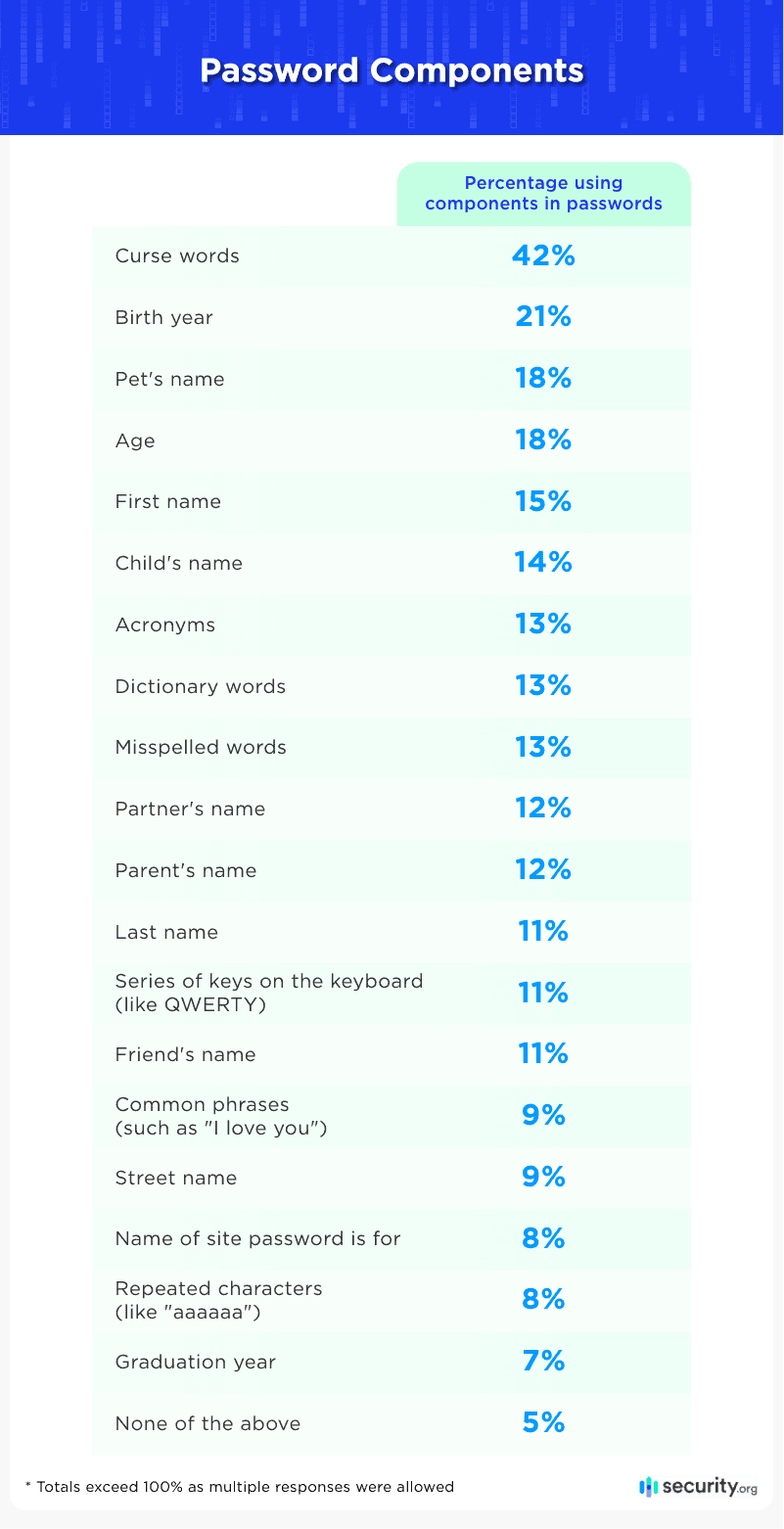
This is especially true when chosen words and numbers aren’t as random as we think. Examining respondents’ sources for passwords, we found several predictable elements:
More than half of people admitted that they use familiar names in their passwords, such as their own name or their children’s or pet’s names. In fact, 15 percent used their own first name in their passwords! Using meaningful names and numbers makes work easier for hackers who may already possess personal data, while sequential keystrokes and “tricky” characters offer little protection from code-breaking programs.
Another 42 percent admitted to using curse words in their passwords, up from just 20 percent of people in our 2020 study. Although these words are probably very memorable for some people, they are vulnerable since they are so commonly used in passwords. Also, think twice before using profanities in your workplace logins since your employer may be able to see them.
Using important names and meaningful numbers might seem like an easy way to help you remember passwords, but they are also very easy for hackers to guess and crack.
Random Password Generators
By far, the safest way to compose strong, unique logins is to use a password generator tool. These programs follow recommended standards, don’t use data tied to the user, don’t rely on real words, and never recycle suggestions. With no patterns, random passwords are hard to guess even with sophisticated password-cracking software.
Our study shows that 27 percent now use password generators, up from 15 percent the previous year. That corresponds with the increase of the use of password vaults, since most password management tools include a random password generator. Web browsers (like Chrome) and operating systems now offer that feature, too.
Outside those, there are other options if you want a free password generator. Even Security.org has a free Random Password Generator tool. Ours can generate passwords from six to 32 characters long and can include uppercase and lowercase letters, numbers, and special symbols.
At a minimum, a secure, randomly generated password must have:
- 12 characters
- An uppercase letter
- A lowercase letter
- A number
- A special symbol
Password Protection Tips
Creating strong passwords is only half the battle, as it’s equally important to keep your logins private and secure.
It was encouraging to learn that many in our research have used two-factor authentication on at least one device or account:
This number may be inflated by counting smartphones that authenticate via fingerprint or face scan by default. Hopefully, a similar proportion of people activate 2FA on all important accounts, which is like adding a deadbolt to back up their keys.
More disheartening was discovering that over a third of Americans continue to share their personal passwords. Unfortunately, this number had jumped significantly since last year.
Part of the rise may be due to increased sharing of streaming service logins during pandemic lockdowns, but even this practice is a security risk that needs to be taken seriously.
Comparing year-over-year results did reveal that password storage methods are gradually improving. While the number of adults relying on memory stayed steady, more users turned to secure digital methods and fewer committed codes to paper or hard drives.
Most of these methods are imperfect. Those memorizing logins tend to reuse simple passwords, while notebooks and Post-Its are inefficient and easily pilfered. Local digital files are better, but remain unencrypted and insecure. Password managers are the best solution for storing complex codes (though browser versions should never be used on shared devices).
The Bottom Line
As greater portions of our personal, professional, and financial lives transpire online, securing data becomes ever more important. The first line of defense for your digital accounts is password protection, so don’t let bad habits make you more vulnerable.
It’s easy to think that hacking won’t happen to you, but 38 percent of those in our study have experienced at least one broken password, and most of those victims had employed bad practices.
It’s little wonder that only 49 percent of Americans strongly believe that their passwords are safe. You may never be able to halt hacking or control all corporate data breaches, but good password habits can keep your information far safer. By following best practices, using password managers, and vigilantly guarding your identity against theft, you can feel more confident about personal digital security.
Best Practices for Your Passwords
The gold standards of password protocols are set by the National Institute of Standards and Technology’s (NIST). Its annual recommendations regularly evolve to keep pace with hacking and countermeasure techniques, but consistently feature these main principles:
- Uniqueness: The first commandment of password creation is to never reuse your logins. Generating unique passwords for every account limits the exposure of any individual code and prevents the bad guys from gaining a master key with one successful hack.
- Strength: Several elements factor into a password’s security, but NIST’s latest guidance concludes that length is the most critical factor. Modern hacking algorithms are hardly slowed by combining symbols, cases, and numbers, but longer codes remain harder to crack. Choose passwords of at least eight characters, but 12 or more is even better.
- Storage: The strongest password does little good if it isn’t kept a secret. Don’t share your logins, don’t commit them to paper, and don’t rely on your memory alone. Password manager tools like Dashlane or NordPass are the best solution (they can also generate and auto-fill your suitably complex codes).
- Authentication: Enabling two-factor authentication (2FA) on accounts adds a failsafe step to further fend off breaches. With 2FA in place, high-risk accounts or suspicious logins require a second-tier identifier (such as a personal security question, a text message, or a face identification) that only you will possess.
- Updates: In the past, experts recommended frequent password changes, but this position was recently reversed by the NIST. The agency found that frequent changes don’t make logins safer and can actually lead to worse password abits. Current guidelines recommend revising credentials if they’re compromised, which makes vigilant monitoring essential. Most password managers track data breaches and will notify you of exposure, and dark web monitors will alert you if your info is for sale on the black market.
Given all of these safety guidelines, you may be wondering whether your current passwords are strong enough. Plug them into our free Password Strength Tool to find out.
Our Data
Using an online survey, Security.org asked 1,012 adults residing in the United States about their password habits when using online accounts in September 2021. They did not share their passwords during the survey.