Data breach – we hear and read about it in the news and data experts warn us about it – but what really is a data breach? And more importantly, how does it affect us, personally?
A single data breach can affect millions of people, and when you look at it like that, your mind might start to downplay the severity of a breach. Having your data leaked along with the data of millions of other people doesn’t seem as personal as a targeted attack. But that’s not true. Data breaches come with severe potential outcomes that affect not only the company whose records have been breached, but also the individuals who’s data was leaked.
In this guide, we’re going to discuss everything there is to know about data breaches – how they start, their consequences, what to do if your data has been involved, and how to protect yourself.

What Is A Data Breach?
Taking it back to basics, let’s first define “data breach”.
Definition
A data breach is a security incident in which a third party accesses data without the consent of the data’s owner, which could be either a business, its customers, or both.
The Equifax data breach in 2017 is an infamous example. Between May and July 2017, private records that contain personal information of 147.9 million Americans, 15.2 million British citizens, and 19,000 Canadian citizens were exposed. The records belonged to Equifax, but the data they contained belonged to customers.
Causes and Methods
There are a few different ways that people can breach data, whether intentionally or accidentally:
- By exploiting system vulnerabilities from out of date software and injecting systems with malware
- By guessing weak or repeated passwords
- By accidentally downloading viruses or malware, a process also called drive-by downloads
- By sending malware via phishing and spam emails1
- By making a mistake like losing paperwork or sending an email to the wrong recipient
- By losing devices or having them stolen.
Targets
Data breaches typically target businesses that hold massive records of customers’ data. Rather than targeting personal data of individuals, identity thieves go for entire databases. But large businesses aren’t the only ones at risk. Identity thieves target small and local businesses, too – a local flower shop with delivery addresses of customers, a small medical practice with the protected health information (PHA) of patients, a private school with records of children and their parents, and so on.
Of course, the real target of those identity thieves is the personal information of individuals. We hear news about large companies suffering breaches, but if you’re a customer of those companies, you should be concerned too.
Phases
Data breaches occur in five major phases, according to cyber security company Cygilant:2
- Target researched: First, hackers research a business: what hardware and software it uses, how much they spend on cyber security by looking at court records and financial filings, and how they can use partners as entry points.
- Vulnerabilities scanned: Next, the hackers scan systems and their open ports, enumerating all devices and accounts on networks to find points of entry.
- Vulnerabilities exploited: After they find these points, they run exploit code.
- Payload delivered: Next, the hackers will either upload malware, take over accounts, hijack servers, or breach data using another method.
- Data extracted: Finally, the hackers download the data they want, be it intellectual property, medical information, or financial information.
What Are The Consequences of Data Breaches?
A data breach can result in many different consequences, mostly negative. And again, these outcomes befall not only the companies to whom the exposed records belong, but also their customers.
- Identity theft: Using customers’ PII, or personally identifiable information, hackers will commit identity theft to file tax returns, secure bank loans or other actions that require PII.
- Financial losses: In 2020, the average cost of a data breach in the U.S was $3.86 million. Now, keep in mind that this includes data breaches from huge companies like Microsoft and Walgreens, which is why the number is so high. Still, it’s clear that data breaches can have pretty extreme financial consequences.
- Loss of productivity: Once a data breach occurs, businesses need to find and fix the vulnerabilities, which can take away from other lucrative pursuits. On average, it takes businesses 280 days to identify and contain data breaches,3 or about three-quarters of a year.
- Ruined credit: For individuals who have had their identities stolen, their credit score may tank, resulting in difficulty getting bank loans, jobs, or even rental agreements.
- Lack of privacy: Depending on the type of information, data breaches may reveal information that people wanted to keep private (like the breach of Ashley Madison, a dating website for people seeking affairs).
- Losing customers: For businesses, data breaches may cause distrust in customers, who may switch to a competitor.
- Damage to reputation: Moreover, data breaches may turn off potential customers from doing business with organizations.
- Loss of intellectual property: The hackers may steal intellectual property, which can result in financial losses and/or expensive lawsuits.
- Online vandalism: Once hackers breach a website, they may vandalize it, which requires more time, money, and energy to restore.
- Ransoms: Ransomware is malware that the hacker refuses to remove unless the breached business pays a monetary ransom.
If there’s one silver lining though, data breaches often shed light to the security practices of companies we deal with. Usually, businesses that experience a breach take steps to patch the vulnerabilities and shortcomings that allowed it to happen. That doesn’t do anything to undo the damages, but it might help prevent future breaches.
How Can I Prevent Data Breaches?
Now, we can’t control how businesses handle the data we provide. They have their own privacy, data collection, and data security policies. And because of that, there’s no way for us as individuals to 100-percent prevent data breaches from occurring. That being said, there are several best practices we can adopt to decrease the likelihood of our data getting leaked in a breach.
General Best Practices
Whether you’re an individual or a business, here are a few ways you can help to prevent data breaches:
-
- Password hygiene: Each of your online accounts should have a strong, complicated, and unique password. To see if your password is up to snuff, use our password strength tool. We also created a password generator tool to help you create strong passwords in a flash.
- Software updates: If you don’t update your software as soon as updates are available, then you are making your system vulnerable to breaches.
- Monitoring financial accounts: Either monitor your financial and bank accounts manually or automatically with the best identity theft protection services.
- Monitor credit: Again, you can either monitor your credit from all three major credit-reporting bureaus manually or with automatic credit monitoring software.
- Secure file storage: Make sure that you store any sensitive information in encrypted vaults, ideally password protected with advanced authentication to prevent unauthorized access.
- Clean up social media: Sometimes, we don’t realize how much information we reveal on social media. From names and birthdays to addresses, make sure that your PII is kept to a minimum on social media and that your accounts are set to private.
>>Further Insight: How to Remove Your Name From the Internet
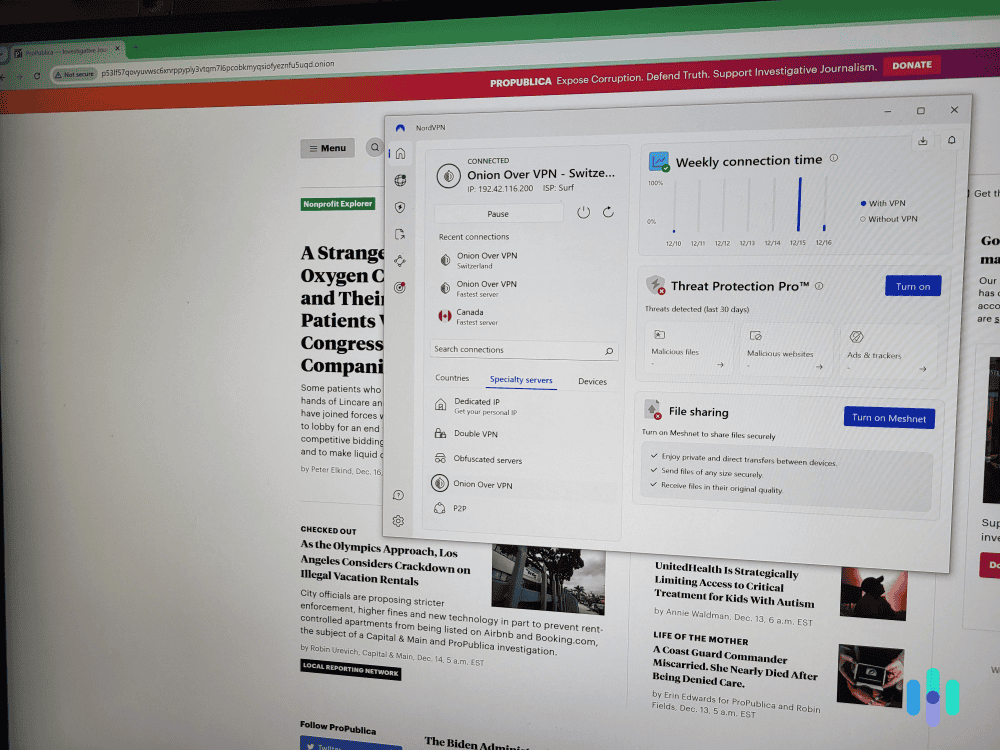
- VPNs: VPNs increase your online safety by encrypting your web activity and IP addresses, which makes it harder for hackers to glean any of your online activity.
- Antivirus software: Finally, antivirus software detects malware and viruses by scanning your devices for suspicious behaviors that could lead to data breaches.
FYI: The majority of most identity theft protection services will monitor your credit scores and reports on Experian, TransUnion, and Equifax, so you probably won’t need a separate credit monitoring software.
Best Practices for Businesses
Businesses need to take their digital security to the next level in order to minimize the risk of breaches, taking steps such as:
- Adhere to state requirements: As you’ll read more below, digital privacy laws differ by state when it comes to storing customer data, so make sure you brush up on your requirements.
- Only store minimal information needed: As a general rule, you should keep as little customer information as possible and store it securely, be it physical or digital data. Some more tips on storing your data:
- Lock up any physical records and restrict access to employees that have been background checked. Don’t give access to any temporary workers or vendors, but rather long-term employees that you can trust.
- Before you throw out any sensitive paper files, shred them. If the data is stored on portable hardware like CDs or DVDs, destroy them before disposal.
- For any data stored on a hard drive, make sure you completely wipe it or even destroy it before disposal, similar to CDs and DVDs.
- If you or your employees ever use a photocopy machine to copy sensitive documents, make sure that the settings clear the data after every use.
- Train employees: Inexperienced or untrained employees are a very frequent cause of data breaches, so make sure to train your employees to:
- Put away files as soon as they’re done using them.
- Log out of computers as soon as they’re done using them, even if it’s just to walk to the water cooler for a few minutes.
- Lock all filing cabinets and offices when not in use.
- Only use work devices for work purposes and not for things like torrenting or using inappropriate websites or unapproved software.
- Never leave laptops or phones unattended.
- Don’t store any personal information on work devices.
- Use work devices even when working remotely, if possible.
- Password protect: Again, password protect all devices and turn on time out functions so that devices lock after periods of non-use.
- Encrypt: All data, including email, should be encrypted both “at rest”, while not in use, and “in motion”, while in use.
- Avoid using portable media: DVDs, CDs, and USB drives should be avoided if you can.4

What To Do If You’ve Been Involved in a Data Breach
Even the most stringent people and businesses can still find themselves involved in data breaches. Don’t panic; with the right steps, you can contain the breach and minimize its financial impact.
For Individuals
For individuals whose information was involved in a data breach, you can protect yourself and your accounts with a few simple steps:
- Contact financial institutions: First, call your bank, credit card company or credit union and alert them of the breach; they can check your account for suspicious activity and if need be, close your account and open a new one.
- Freeze credit reports: Freezing your credit report means that identity thieves won’t be able to open accounts in your name. And no, it won’t affect your credit score. To freeze your reports, contact the credit bureaus directly either online or over the phone:
- Equifax
- Equifax.com/personal/credit-report-services
- 800-685-1111
- Experian
- Experian.com/help
- 888-397-3742
- Transunion
- TransUnion.com/credit-help
- 888-909-8872
- Equifax
Did You Know: Freezing your credit won’t affect your credit score one way or the other.
- Depending on which information was exposed: Your actions will differ based on what data of yours was exposed.
- Social Security number: If your SSN was exposed, first check your credit for unfamiliar accounts or charges. We recommend again, freezing your credit, but if you’d rather not, at least put out a fraud alert. Fraud alerts mean that businesses will need to contact you before issuing credit; they last for a year before you can get a new one. To create a fraud alert, contact the credit bureaus using the above contact information. We also recommend filing your annual tax return as soon as possible so that no one else can file one with your information or use your SSN to secure a job.
- Online username and/or password: Having your username and password breached is a much better situation than having your SSN breached. All you have to do is change your password and your username, if possible. If you can’t log into your account to change these credentials, contact the company to either recover or shut down your account. As well, if you used the same breached password for any other online accounts, change it so that each account has a unique password. Finally, check your bank and credit card accounts for any suspicious charges that you don’t recognize.
- Bank account, credit, or debit card information: While this scenario may sound scary, all you’ll have to do is contact your bank or credit company to close and replace your account or card.
>>Related Reading: How to Remove Your Address From the Internet
For Businesses
When it comes to data breaches, things are much more difficult on the side of the business than they are on the side of the customer, so much so that it may be worth it to hire cyber security professionals to help you out. Nevertheless, here’s a brief overview of what’s involved.
- Fix vulnerabilities: While this may sound obvious, your first step should be to fix the vulnerabilities to prevent further data loss, which again, could require hiring a forensics team or legal counsel.
- Secure physical areas: Make sure that your office is physically secured and change all access codes.
- Remove improper information: If your website was vandalized, remove all vandalism and any false or malicious information from other websites by contacting them directly.
- Interview people who discovered breach: Whoever discovered the breach probably has better insight into its causes than most, so make sure to talk with them about it extensively.
- Do not destroy the evidence: Hard as it may be, try not to tamper with evidence, as it could be used to catch the perpetrator.
- Notify affected customers and relevant agencies: You may have to either notify your customers or government agencies about the breach, depending on your state’s laws.
Speaking of…
The Laws Surrounding Data Breaches
Whether you’re preventing a data breach from happening or dealing with the after-effects, make sure you’re adhering to state and federal data breach notification laws.
Federal
Most federal data privacy legislation only applies to the healthcare and financial industries; there’s no federal legislation specific to data breach notifications, which are handled at a state level.
State
Each state has its own unique data breach notification laws, and while all states have some form of this law, the requirements differ state-by-state. For the most part, however, businesses are legally required to inform their state’s residents of data breaches as soon as possible.
| State | Required to Alert Customers of Data Breaches? | Maximum Amount of Time To Notify Customers of Data Breach |
|---|---|---|
| Alabama | ✓ | As soon as possible |
| Alaska | ✓ | As soon as possible |
| Arizona | ✓ | 45 days |
| Arkansas | ✓* if it affected over 1,000 people and had a “reasonable likelihood of harm” | As soon as possible |
| California | ✓* if it affected over 500 residents | As soon as possible |
| Colorado | ✓ | 30 days |
| Connecticut | ✓* if breach will likely result in harm | 90 days |
| Delaware | ✓ | 60 days |
| Florida | ✓* if it affected 500 people or more | 30 days |
| Georgia | ✓ | As soon as possible |
| Hawaii | ✓ | As soon as possible |
| Idaho | ✓ | 1 day |
| Illinois | ✓ | As soon as possible |
| Indiana | ✓ | As soon as possible |
| Iowa | ✓* if it affected over 500 residents | 5 business days |
| Kansas | ✓ | As soon as possible |
| Kentucky | ✓ | As soon as possible |
| Louisiana | ✓ | 60 days |
| Maine | ✓ | As soon as possible |
| Maryland | ✓ | 45 days |
| Massachusetts | ✓ | 10 business days |
| Michigan | ✓ | 3 business days |
| Minnesota | ✓* only applies to government agencies | As soon as possible |
| Mississippi | ✓ | As soon as possible |
| Missouri | ✓ | As soon as possible |
| Montana | ✓ | As soon as possible |
| Nebraska | ✓ | As soon as possible |
| Nevada | ✓ | As soon as possible |
| New Hampshire | ✓ | As soon as possible |
| New Jersey | ✓ | As soon as possible |
| New Mexico | ✓ | 45 days |
| New York | ✓ | As soon as possible |
| North Carolina | ✓ | As soon as possible |
| North Dakota | ✓* if it affects 250 or more residents | As soon as possible |
| Ohio | ✓ | 45 days |
| Oklahoma | ✓ | As soon as possible |
| Oregon | ✓* if it affects 250 or more residents | 10 days |
| Pennsylvania | ✓ | As soon as possible |
| Rhode Island | ✓ | As soon as possible |
| South Carolina | ✓* if it affects 250 or more residents | 3 days |
| South Dakota | ✓ | 60 days |
| Tennessee | ✓ | 45 days |
| Texas | ✓* if it affects 250 or more residents | 60 days |
| Utah | ✓ | 20 days |
| Vermont | ✓ | 45 days |
| Virginia | ✓ | As soon as possible |
| Washington | ✓* if it affects 500 or more residents | 30 days |
| West Virginia | ✓ | As soon as possible |
| Wisconsin | ✓ | 45 days |
| Wyoming | ✓ | As soon as possible |
The Biggest Data Breaches
Even large companies like Facebook aren’t immune to data breaches. Here are the biggest data breaches of the past few years, according to CNBC.5
| Company | Year(s) of Data Breach | Number of Records Breached | Reason for Breach |
|---|---|---|---|
| Yahoo | 2013, 2014 | 3 billion, 500 million | Hacking |
| First American Financial Corp | 2019 | 885 million | Poor security |
| 2019 | 540 million | Poor security | |
| Marriott International | 2018 | 500 million | Hacking |
| Friend Finder Networks | 2016 | 412.2 million | Poor security, hacking |
Recap
And that’s it for our guide to data breaches. To learn more about how to protect yourself online, read our guide to digital security or, for more information on data breaches, keep reading below.
Have you been involved in a data breach? If you’re looking to remove your personal information from the internet, there are digital tools that can help.
FAQs
We’ve received a lot of questions about data breaches, so we’re hoping to knock them all out here.
-
What happens in a data breach?
During a data breach, hackers steal a business’ data, which may include customer information, by breaking into vulnerable systems.
-
What does “data breach” mean?
“Data breach” means that a company’s database has been compromised, or breached.
-
What is the most common cause of a data breach?
While we can’t say for sure what is the single most common cause of a data breach, the most common causes are weak credentials, system vulnerabilities and human error.
-
Why is a data breach bad?
Data breach is bad because it exposes the personal information of customers and businesses, which can be used for identity theft and theft of intellectual property, among other negative consequences.