NordStellar Review 2025 — Is It Right for Your Business?
NordStellar’s in-depth dark web monitoring makes it one of the best proactive security solutions on the market in 2025.
What We Like
- Monitors the dark web in real time. NordStellar continuously scans tons of cybercrime communities and channels on the dark web for leaked data and keywords associated with your brand.
- Provides valuable insights about vulnerabilities. NordStellar helps your security team understand how cybercriminals target your company. It provides information about how, when, and why past vulnerabilities happened.
- Uses password fuzzing to protect against weak logins. The provider uses advanced cracking methods to generate and block variations of previously-compromised passwords, preventing anyone from accidentally using them.
What We Don't Like
- Lacks attack path analysis. This is a feature that could make it even easier for your security team to anticipate cyberattacks and stay ahead of evolving threats.
- Isn’t bundled with NordLayer. NordLayer is developed by the same company behind NordStellar (Nord Security). NordLayer is actually intended to be used together with NordStellar, since it provides endpoint and network security. We’d like to see Nord Security include both services in a bundle to provide the best value.
Bottom Line
NordStellar is among the best threat exposure management platforms in 2025. It provides excellent identity protection, proactive asset security, cyber threat insights, and data breach monitoring.
NordStellar comes with:
- Dark web monitoring — It continuously scans dark web cybercrime communities for leaked data and mentions associated with your brand.
- Data breach monitoring — NordStellar provides insights about threats targeting your organization and past security incidents.
- Account takeover prevention — NordStellar scans for compromised accounts and login credentials, and prevents the use of leaked logins.
- Session hijacking prevention — The platform detects stolen session cookies and revokes compromised user sessions.
We only have minor complaints. First, NordStellar doesn’t include attack path analysis (many of its competitors have this). Also, it’s not bundled with NordLayer, which provides endpoint and network security, and is developed by the same company that makes NordStellar (Nord Security).
NordStellar has a customizable pricing model, and it also has a free demo, which we took part in to assess just how well it can protect businesses. Find out more as we unpack NordStellar for you.
NordStellar Pricing
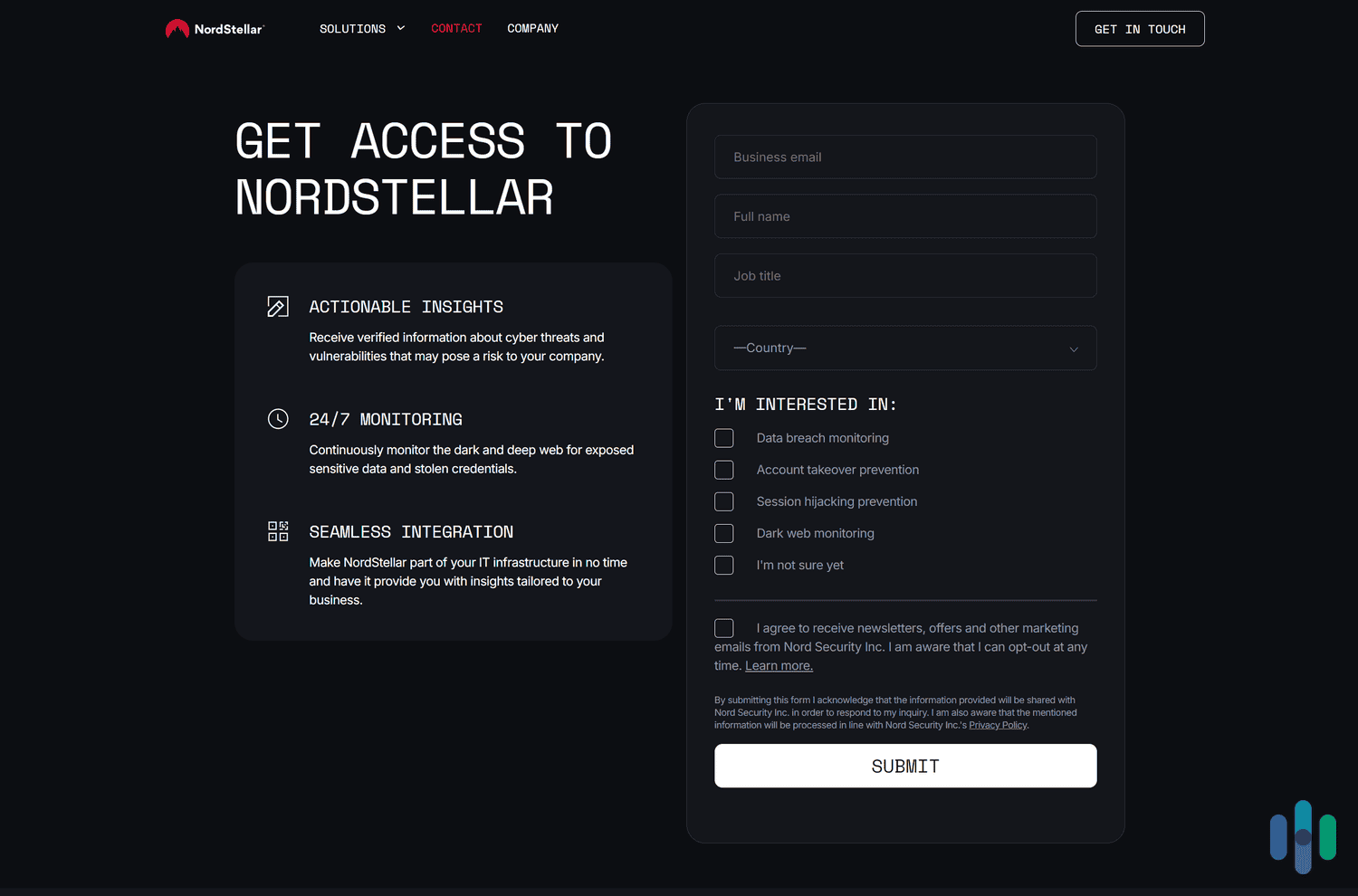
NordStellar doesn’t show subscription costs on its website. Instead, you’ll need to contact the provider, and its sales reps will find the best pricing model for you depending on your company’s cybersecurity needs. This is pretty standard with threat exposure management solutions, as other competitors (like Darktrace, Cymulate, and Tenable One) don’t display pricing plans on their sites either.
Like most threat exposure management platforms, NordStellar provides access to a free demo. To get access to the demo, you’ll need to contact NordStellar via a form, and provide your business email, full name, job title, and location. A NordStellar representative will get in touch with you afterward.
FYI: You may have to be patient. NordStellar took about a week to respond to our request for a demo.
NordStellar Features
NordStellar lets you secure company assets and allows your security team to proactively detect potential cyber threats — it also makes it easy for them to take appropriate measures to stop the threats from causing financial and reputational damage to your company.
The platform monitors your brand’s external-facing assets (including IP addresses, domains, and cloud resources), detecting vulnerabilities and assessing risk posture while doing so.
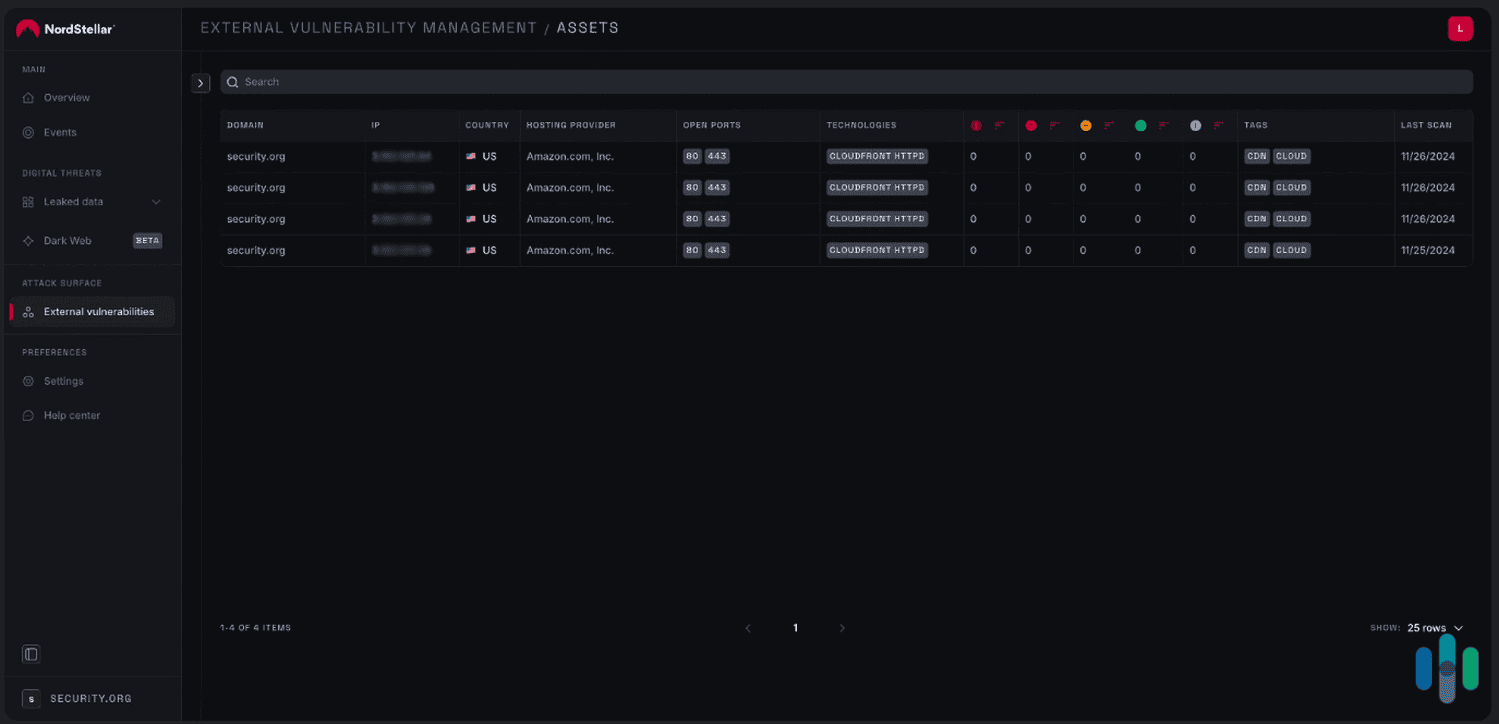
NordStellar also scans the dark web for data associated with your organization and provides your security team with valuable insights about how past vulnerabilities happened. What’s more, it provides access to tools that protect company, partner, and customer accounts against account takeovers and session hijacking.
Below, we’ll take a closer look at the provider’s key features:
Data Breach and Dark Web Monitoring
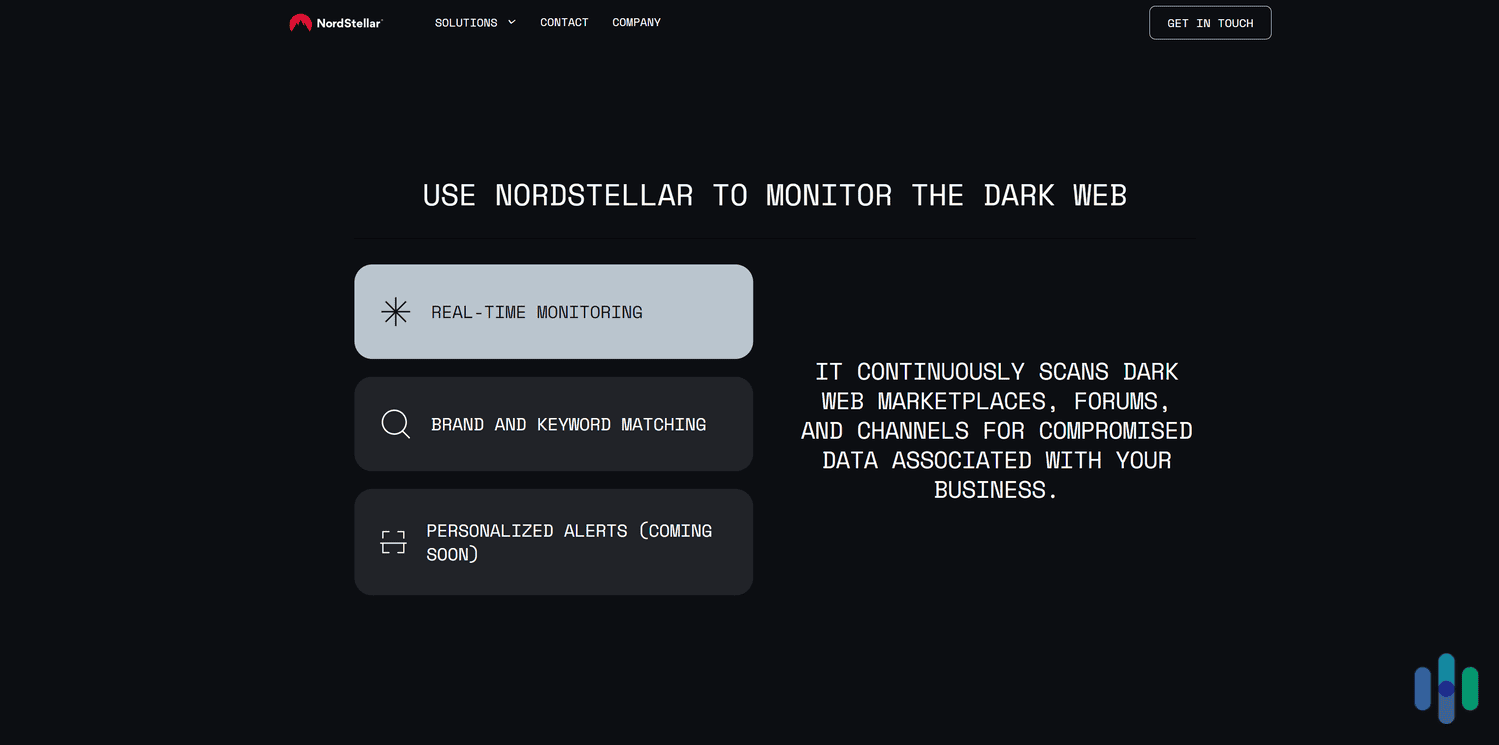
NordStellar provides real-time dark web monitoring and valuable insights about data breaches. It also sends alerts about potential cyber threats targeting your company — such as data leaks, phishing attacks, and mentions of your brand in cybercriminal communities. This lets your security team proactively detect cyberattacks and vulnerabilities, allowing them to prevent leaks from happening or escalating into major security incidents that put your company’s data and reputation at risk.
In addition to scanning for company data, NordStellar also uses predefined sets of keywords that are related to your brand, partners, and industry when monitoring cybercrime communities. This ensures that NordStellar only flags relevant threats that don’t waste your security team’s time.
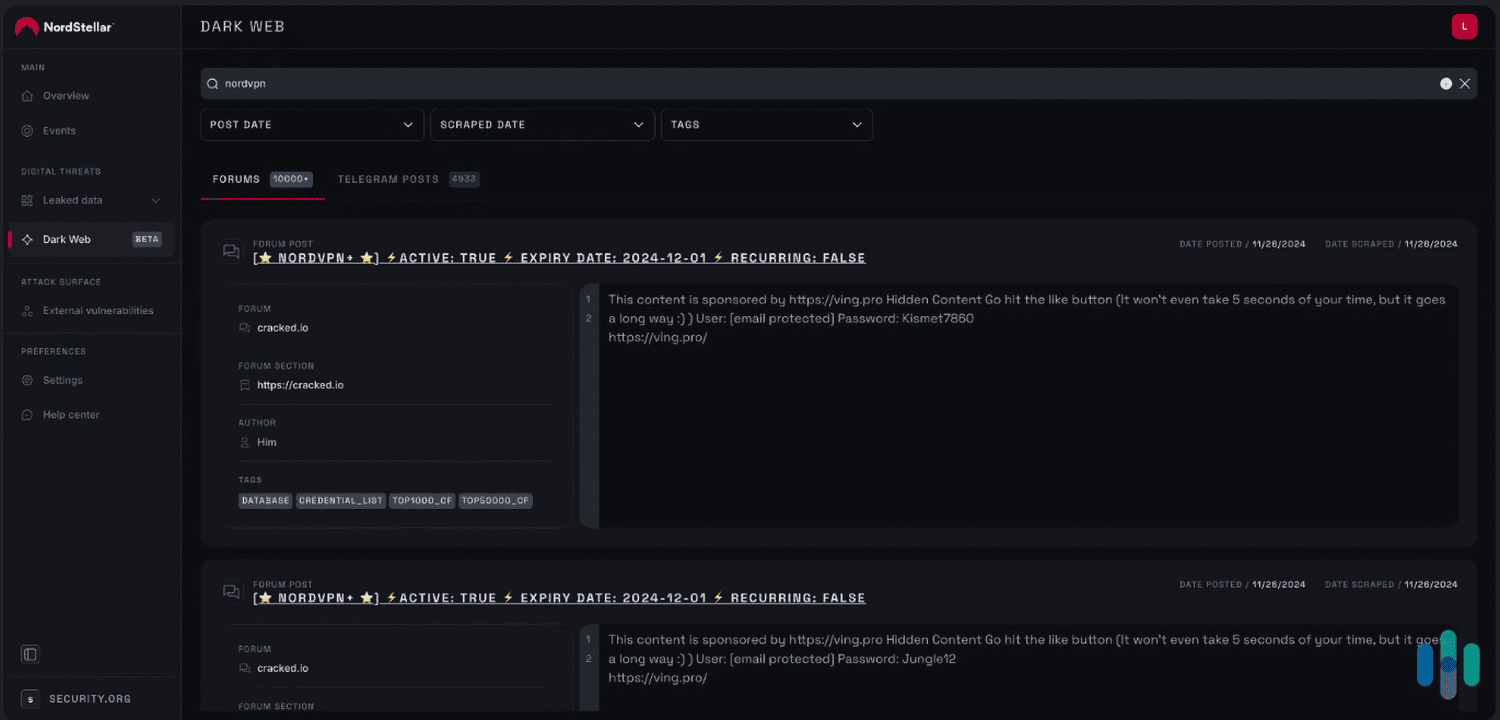
NordStellar boasts one of the largest dark web data pools on the market. The provider monitors thousands of cybercriminal communities across the dark web ecosystem, such as dark web forums, dark web search engines, illegal markets, ransomware blogs, hacking manuals, and more. On top of that, it also monitors cybercrime Telegram channels.
FYI: As you can see in the screenshot below, NordStellar’s dark web monitoring also features a search function so you can manually monitor your own keywords. This can prove useful for companies that offer digital products like software, as it allows them to detect unauthorized distribution.
This feature also helps your security team improve its cybersecurity strategies. That’s because NordStellar provides valuable insights about past vulnerabilities, including how malicious actors exploited them, when the attack occurred, and why it happened. In addition, the service sends updates about what tactics cybercriminals use to target your business (like phishing, malware distribution, or coordinated attacks, for example).
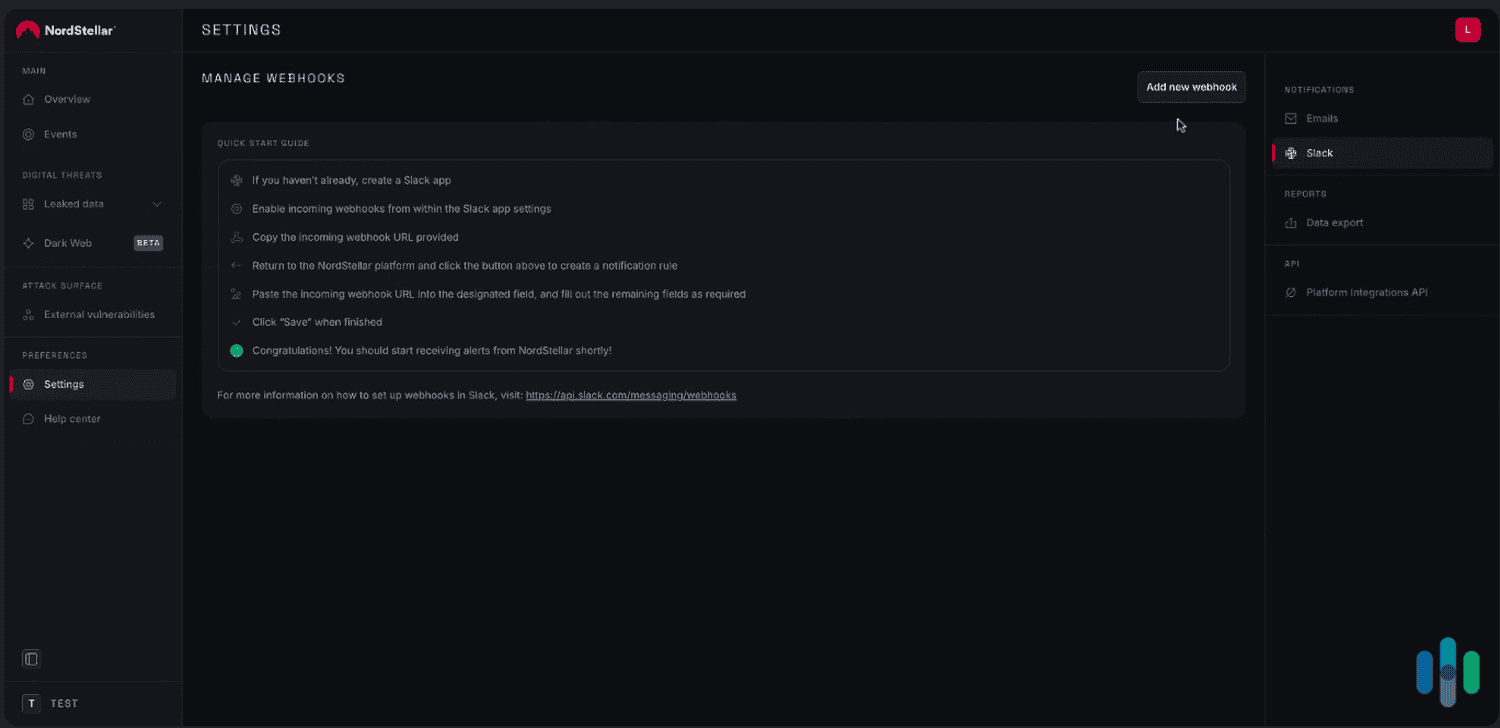
NordStellar is also planning on implementing personalized alerts in the near future. This would allow you to configure the service to monitor specific brand-related keywords and phrases, and receive alerts when NordStellar detects them on the dark web. In the demo, NordStellar showed us how to set up alerts delivered via Slack, which enabled our IT team to receive real-time alerts without having to leave NordStellar open on their devices.
Overall, we think this feature is excellent for proactive data security. It’s also something you won’t get with many of NordStellars competitors (like Tenable One, Assetnote, or Darktrace). And the few competitors that do have this feature (like Cymulate) only provide limited dark web monitoring since they use small dark web data pools.
>> Read More: What Is the Dark Web?
Account Takeover Prevention
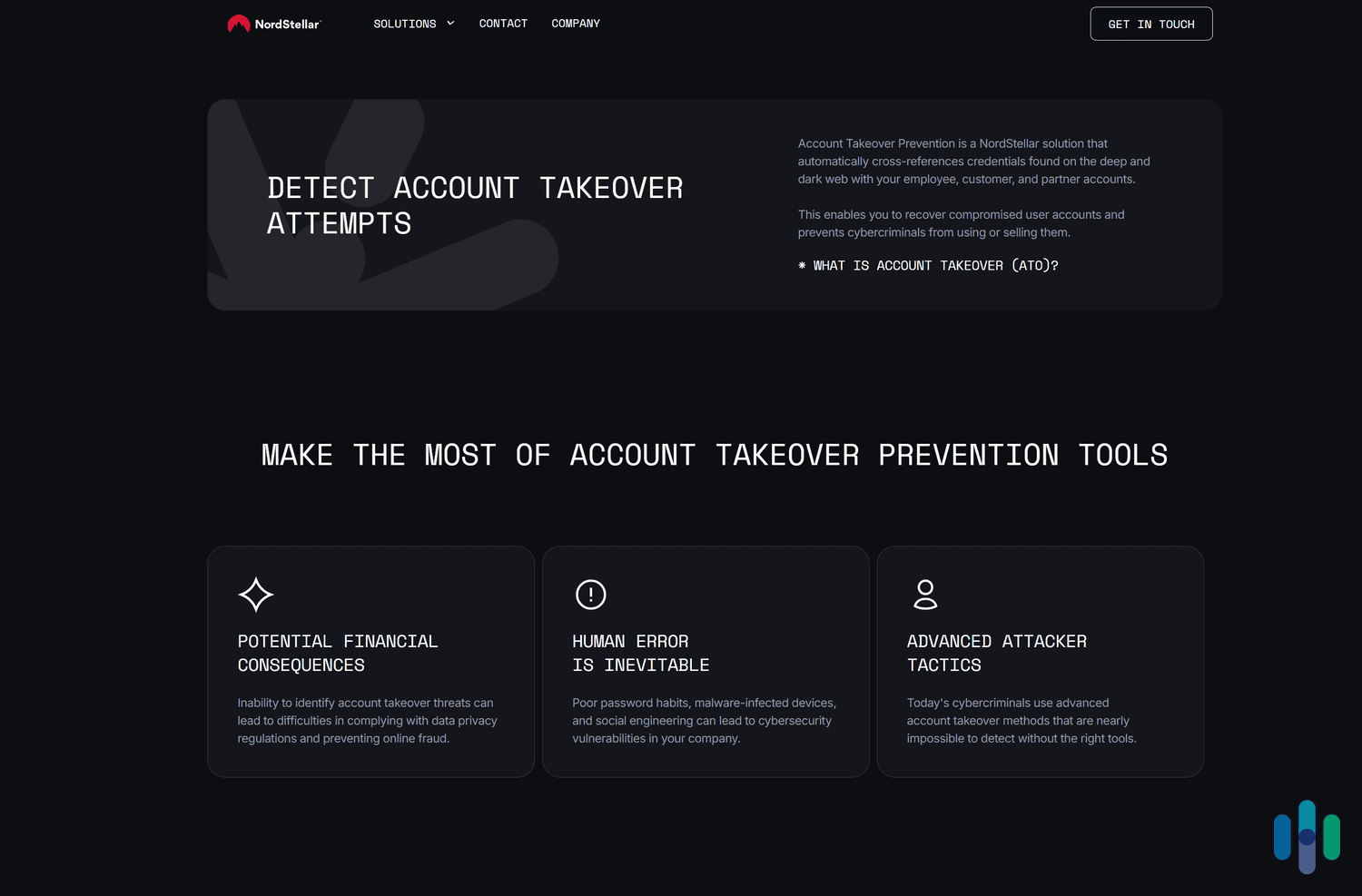
NordStellar protects against account takeover attacks, where malicious actors use various cyberattacks (like credential stuffing or brute-force attacks) to take over corporate, partner, or customer accounts. This protects your company from significant financial losses, reputational damage, and difficulties in complying with data privacy regulations.
The provider’s dark web monitoring feature comes into play here, as it’s used for proactive user scanning. Basically, NordStellar scans for compromised accounts and login credentials on the dark web, and then cross-references your business, partner, and customer accounts with them. It then alerts your security team about potential threats, allowing them to stop unauthorized parties from compromising company and user data.
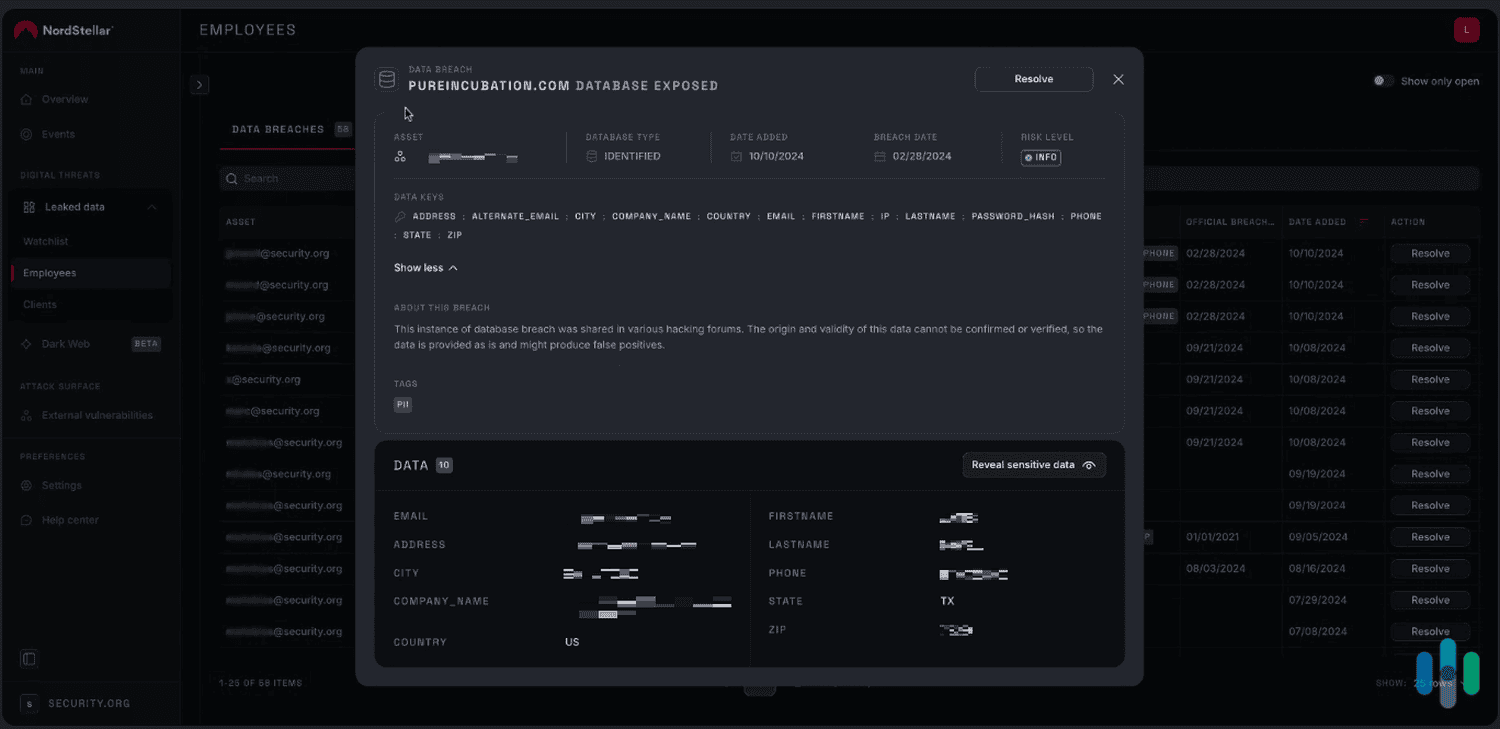
We also like how NordStellar prevents the use of breached login credentials. It monitors user account registration pages and login and password change forms, and runs checks on them to prevent compromised credentials from being used.
The provider also relies on password fuzzing to prevent users from unknowingly creating vulnerable passwords. NordStellar analyzes passwords that have been previously compromised, and generates variations of those passwords via advanced cracking methods. It then automatically prevents anyone from creating and using such logins.
All in all, NordStellar makes it easy for your security team to enforce security measures that protect company, partner, and user accounts. And since NordStellar prevents the use of breached or vulnerable credentials, it significantly limits the disruptions that could be caused by compromised accounts, ensuring business continuity.
Session Hijacking Prevention
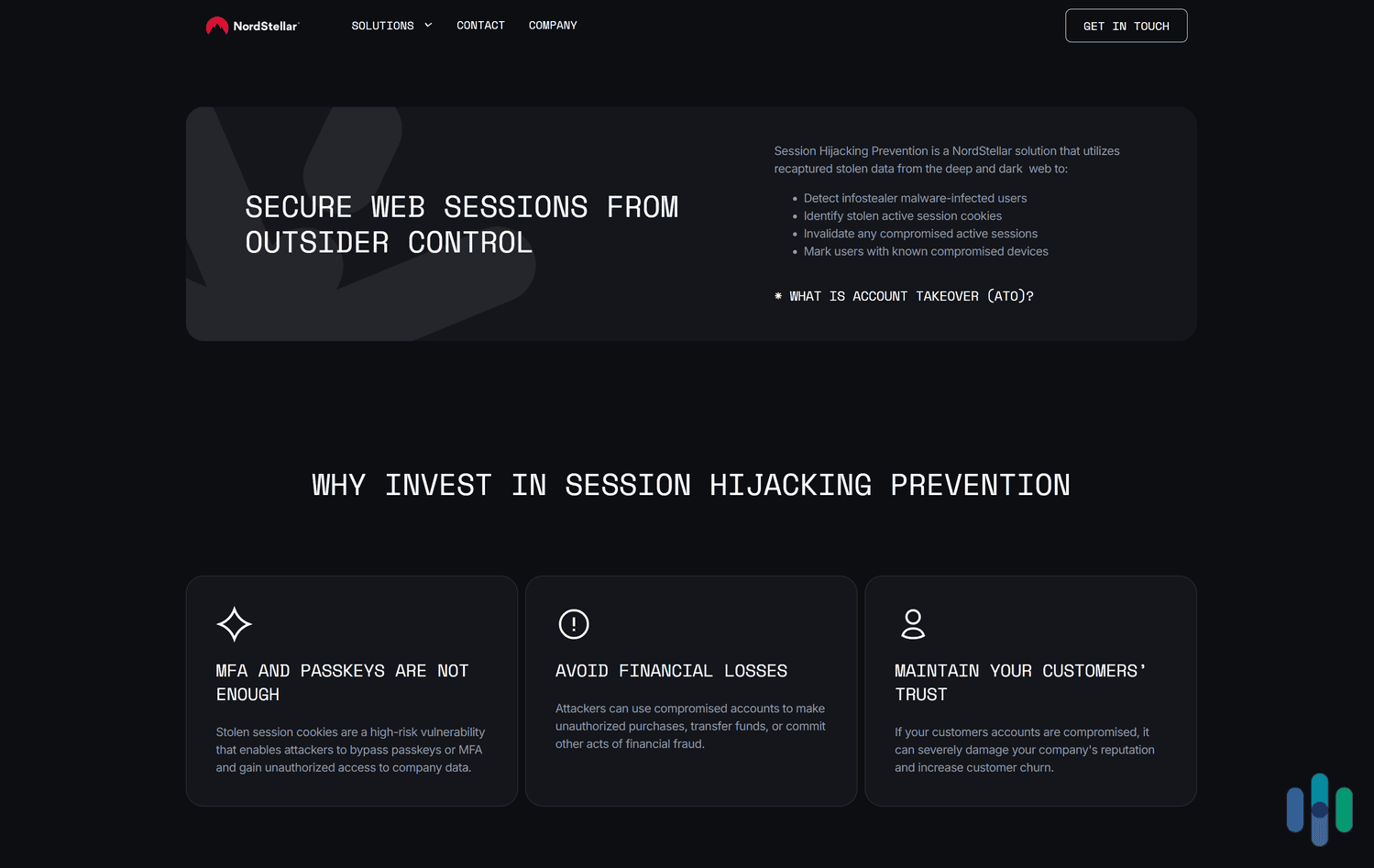
NordStellar uses recaptured stolen data (like session cookies) from the dark web to detect compromised accounts and devices. This stops malicious actors from accessing company resources, such as internal networks and cloud-based platforms. It also protects employees and users from identity theft, prevents account fraud (like unauthorized transactions), and stops unauthorized parties from accessing high-value assets like email addresses, phone numbers, and credit card details.
FYI: Session hijacking is when a malicious actor takes over a user’s active session by compromising their unique session ID. The hacker essentially impersonates the user, taking over their account.
NordStellar leverages its advanced dark web monitoring to scan cybercrime communities and channels for session cookies associated with your employees and customers. When the provider detects a stolen session cookie, it immediately sends you an alert. And the alerts are actionable since they include valuable insights, such as the source of the session cookie and the device it was compromised on.
We also like how NordStellar can invalidate any active session that uses stolen session cookies. This allows your security team to stop cybercriminals from compromising company or customer data even if they’ve already taken over an employee or customer account.
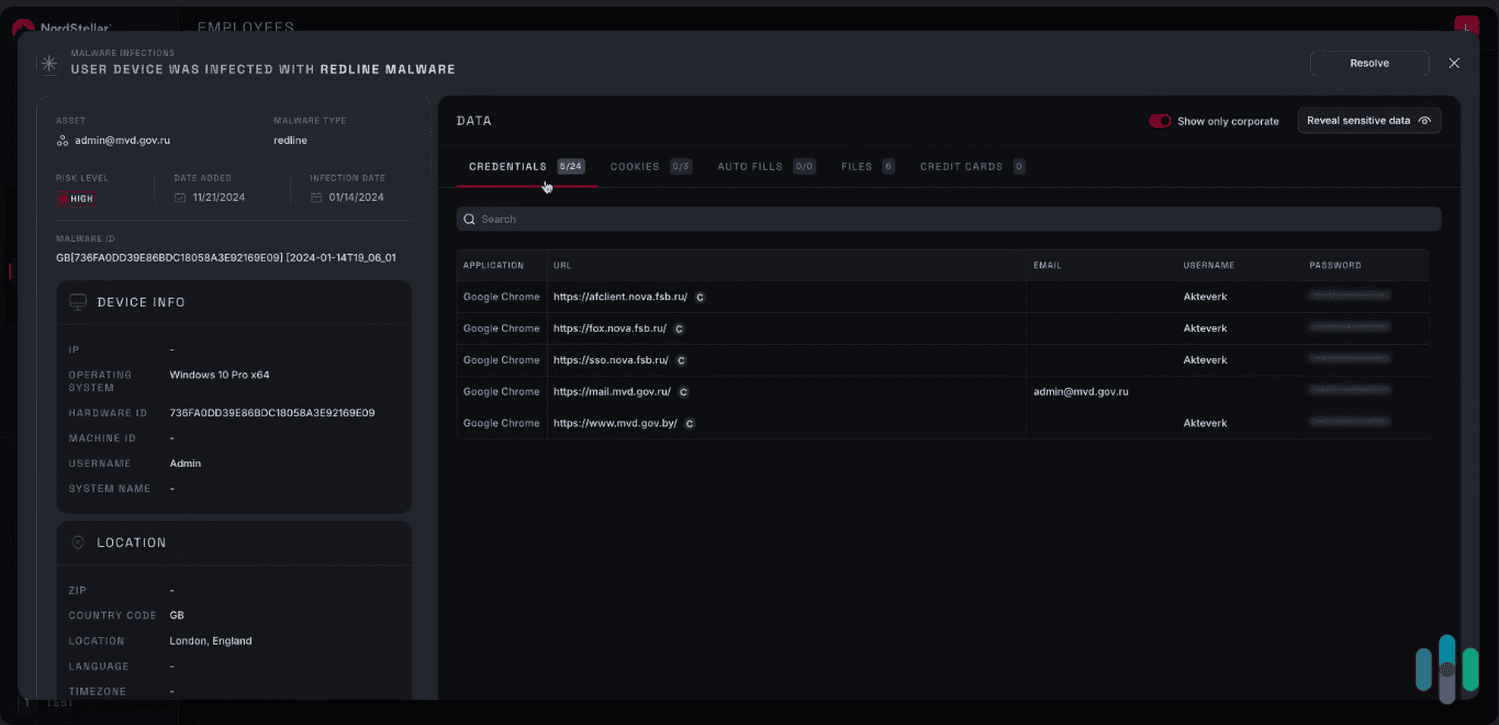
It’s also great that NordStellar lets your team mark users with compromised devices. If it’s a customer device, you can immediately alert the user about a potential malware threat on their device. And if it’s an employee device, it could highlight a need to strengthen the company’s endpoint security strategy.
Overall, we’re very happy to see this feature. Stolen session cookies are a serious cybersecurity risk, mainly because they could allow malicious actors to bypass authentication methods, such as multi-factor authentication (MFA) and passkeys.
What We’d Like to See NordStellar Improve
Our main complaint about NordStellar is that it’s missing attack path analysis. This is a cybersecurity feature that allows your security team to detect and map potential routes that cybercriminals could use to compromise your company’s network. Basically, it lets your team see what malicious actors see when they target your company.
Attack path analysis could empower your security team to be even more proactive when it comes to detecting and preventing threats. It could allow them to easily map the attack paths that pose the greatest risk to your company. This way, you would be able to efficiently allocate resources to prevent high-risk attacks.
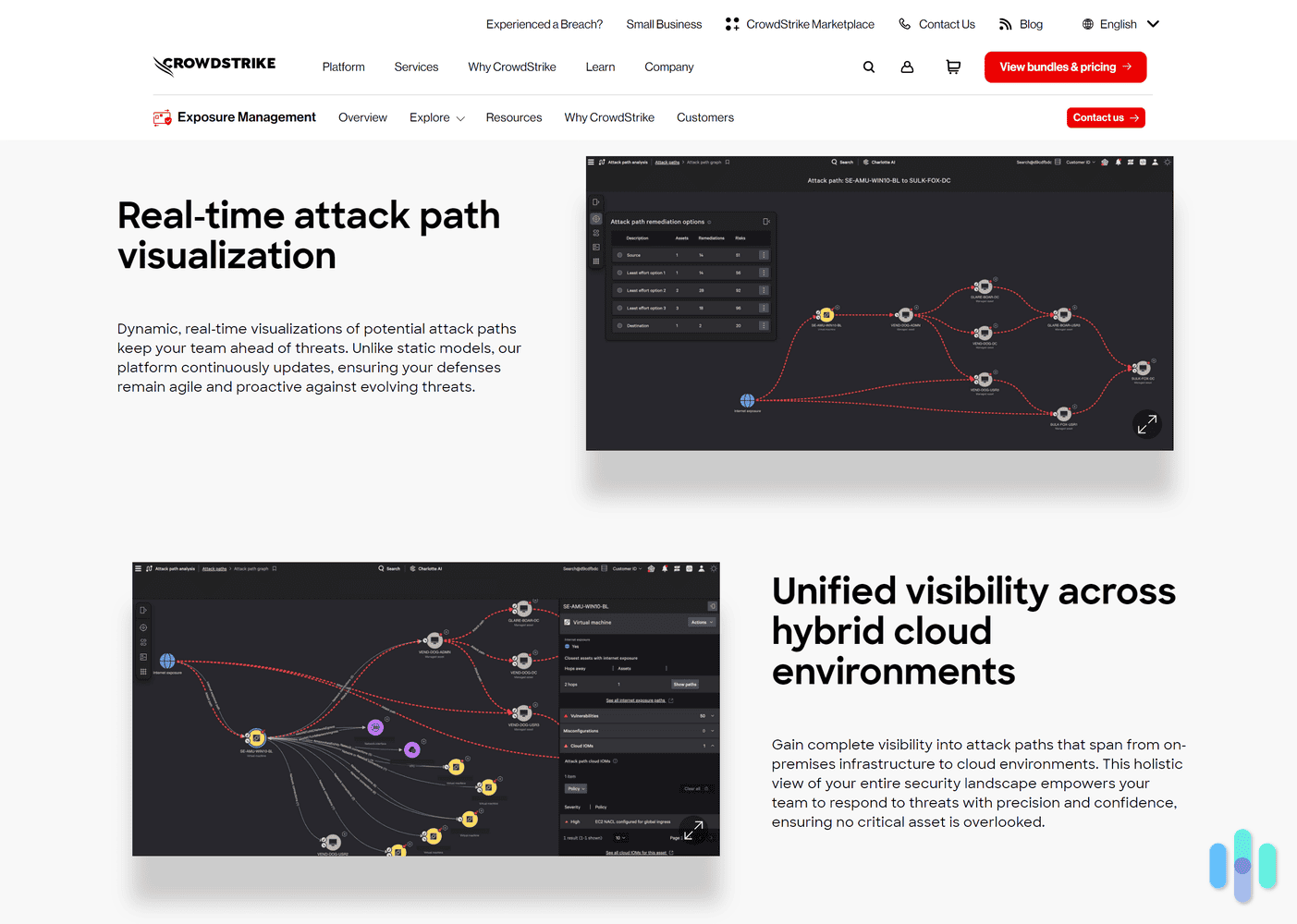
A lot of NordStellar’s competitors provide access to attack path analysis. Some notable examples include Darktrace, Tenable One, and CrowdStrike — CrowdStrike especially stands out since it provides real-time, dynamic attack path visualization that is continuously updated.
Another minor issue is that there’s no way to bundle NordStellar with NordLayer — you need to get each service separately. NordLayer should actually be used together with NordStellar, as it provides endpoint and network security.
Final Thoughts: Is NordStellar a Good Threat Exposure Management Solution in 2025?
NordStellar is an excellent threat exposure management platform. It provides real-time dark web monitoring (and it scans tons of cybercrime communities and channels), it lets your security team analyze past vulnerabilities and learn how malicious actors target your brand, and it protects against account takeover and session hijacking. Just keep in mind you won’t get access to attack path analysis — if this is a deal-breaker, consider other options like CrowdStrike or Tenable One instead.
For the best results, we recommend using NordStellar together with NordLayer. NordStellar helps your security team stay proactive against cyber threats, whereas NordLayer provides network and endpoint security. Just keep in mind that there’s no way to get a NordStellar and NordLayer bundle, so you need to get both services separately.
NordStellar Frequently Asked Questions
-
Can NordStellar monitor the dark web?
Yes, NordStellar provides access to in-depth dark web monitoring. It scans the dark web in real-time for leaked data and mentions associated with your company. Also, the provider uses a very large data pool — it scans dark web forums, illegal marketplaces, dark web search engines, cybercrime Telegram channels, hacking manuals, and more.
-
How does NordStellar prevent account takeovers?
NordStellar does this by scanning the dark web for user accounts and logins associated with your organization — if it detects anything, it alerts your security team. It also prevents the use of compromised logins, and stops users from setting up vulnerable passwords. NordStellar can also detect stolen session cookies on the dark web, and revoke any sessions that use them.
-
Does NordStellar provide access to attack path analysis?
No, NordStellar doesn’t include this feature yet. If this is a deal-breaker for you, there are a lot of decent competitors that provide access to this tool, like CrowdStrike or Tenable One.
-
Does NordStellar have a free demo?
Yes, the platform provides access to a free demo. To access it, you’ll need to fill out a contact form on NordStellar’s site — you’ll have to provide your business email, full name, job title, and location. After that, a NordStellar representative will get in touch with you.
-
What insights does NordStellar provide about cyber threats?
NordStellar scans the dark web and alerts you when it detects compromised assets or keywords related to your brand — this essentially signals that your organization could be targeted by cyberattacks. NordStellar also provides updates about what tactics hackers could use to target your brand (for example, ransomware or phishing). It also helps your security team understand how, why, and when past vulnerabilities happened.