Because they concern complex and technical issues, digital security threats can be much harder to get your head around. However, the impacts of these threats are very real. Even worse, digital threats are all around us, lurking in our inboxes, text messages, and on social media.
Despite digital threats being serious and widespread, we don’t take them as seriously as we should . For example, one recent poll found 66 percent of small business thought leaders saying cyberattacks are unlikely1. Other polls, however, paint a different picture. Surveys routinely show around 17 percent of people saying they’ve been victimized in a cyberattack, and the same percentage say they aren’t sure, which is arguably more concerning2.
If you’ve only given digital security a passing thought, it’s time to start getting more serious. As digital security experts with decades of combined experience, we have put together this guide to make you more informed and adept at your digital security.
What Is Digital Security?
In a nutshell, digital security means protecting your computer, mobile devices, tablets, and any other Internet-connected devices from intruders, which could be in the form of hacking, phishing, and more. Digital security could also be used to protect your personal data from being used and sold by companies. There are a number of ways to protect yourself online, from VPNs to password managers to password generators and identity monitoring services. First, let’s talk more about the threats at hand.
Cyber Attack Statistics
From 2019 to 2023, the FBI’s Internet Crime Complaint Center (IC3) recorded a total of 3.79 million cyberattack complaints, an average of about 758,000 per year.3 To put that into perspective, the FBI received one report roughly every 43 seconds. Those statistics likely underrepresented the scale of the problem because many cyberattacks go unreported.
Even more concerning is the amount of money lost to cybercrime. According to the same FBI report, the 3.79 million complainants translated to a total five-year loss of $37.4 billion. That’s an average loss of about $9,868 per complaint.
The biggest losses come from internet scams, fraud, and identity theft. These are the “big three” of cyber crime, and they can all stem from identity theft. Scammers use breached data to target victims, fraudsters use stolen identities to commit insurance fraud and other types of fraud, and identity thieves make money by selling stolen identity or make fake identities to do things like take out loans.
In a report by the Federal Trade Commission (FTC) in December 2022, it highlighted that people under 60 years old are four times more likely to report losing money to online fraud than those over 60. On the other hand, while they are less likely to report losses, those over the age of 60 generally report higher losses with a median reported loss of $800 each.4 Either way, statistics show that no one is safe from cyber crime.
Fortunately, there are ways to prevent cyber attacks, hacking, phishing, and the like. Read on to find out how from our cybersecurity experts.
What Is Hacking? And How To Avoid It
When you hear the word “hacker,” you probably think of a guy in a black hoodie, slumped over a computer, furiously writing code. And while that may be the case for some hackers, they actually come in all shapes, sizes, and levels of ethics. But before we get into that, we want to address the general question on everyone’s mind, namely—what is hacking?
What Is Hacking?
Hacking is the practice of using knowledge of technology to break into computer systems, exploiting their vulnerabilities. The hacker, the person who performs the hack, might block access to the system, gather data within the system, or gain access to other devices within the same network.
Types of Hackers
Like we said before, not all hackers are created equal. Typically, they are split into three categories: white hat, black hat, and grey hat.
- White Hat Hackers: White hat hackers are the “good guys”. They hack into a company’s website or online infrastructure, but rather than exploit the vulnerabilities they find, they report them to the company so the company can issue security fixes. White hat hackers are typically hired by companies themselves or they might operate through bug bounty programs, where a company offers money to anyone who can find a vulnerability. Even cybersecurity has been impacted by the gig economy!
- Black Hat Hackers: Black hat hackers are the exact opposite. They are the “bad guys,” so to speak, as they hack into systems illegally for reasons of personal gain. Basically, they exploit system vulnerabilities to find personal information to steal, datasets to leak that result in data breaches, or hold websites or data for ransom.
- Gray Hat Hackers: Like anything in life, hacking has a gray area. Gray hat hackers don’t exactly follow ethical standards or even laws when hacking, but many of them believe that what they do is necessary to make the internet — and the world — safer. They usually mean no harm, at least to the general public, but the cybersecurity world typically views their methods unethical. Anonymous is an example, a “hacktivist” group that targets individuals and organizations that they deem bad for the society.
Types of Hacks
Along with these types of hackers come types of hacks, which can generally be split into two categories.
- Zero-Day Hacks: Zero-day hacks include vulnerabilities that the company has never seen before. In fact, the company may not even be aware that they’ve been hacked. Black hat hackers usually save zero-day hacks for companies that they can stand to gain from personally, be it an international business or a national security system. It’s organizations like these that promise huge financial returns— that is, if you don’t get caught.
- Miscellaneous Types Of Hacks: Every other type of hack often uses what’s called a script kiddie, pre-existing software that doesn’t require much programming knowledge in order to attack a system. Unlike zero-day hacks, script kiddies are pretty easy for systems to protect themselves against if the software has been updated5. So be sure to do those software updates, no matter how inconveniently timed they might be!
How Hacking Works
Just how do these hackers find vulnerabilities in systems, exploit them, and gain personally? Three major routes reign supreme:
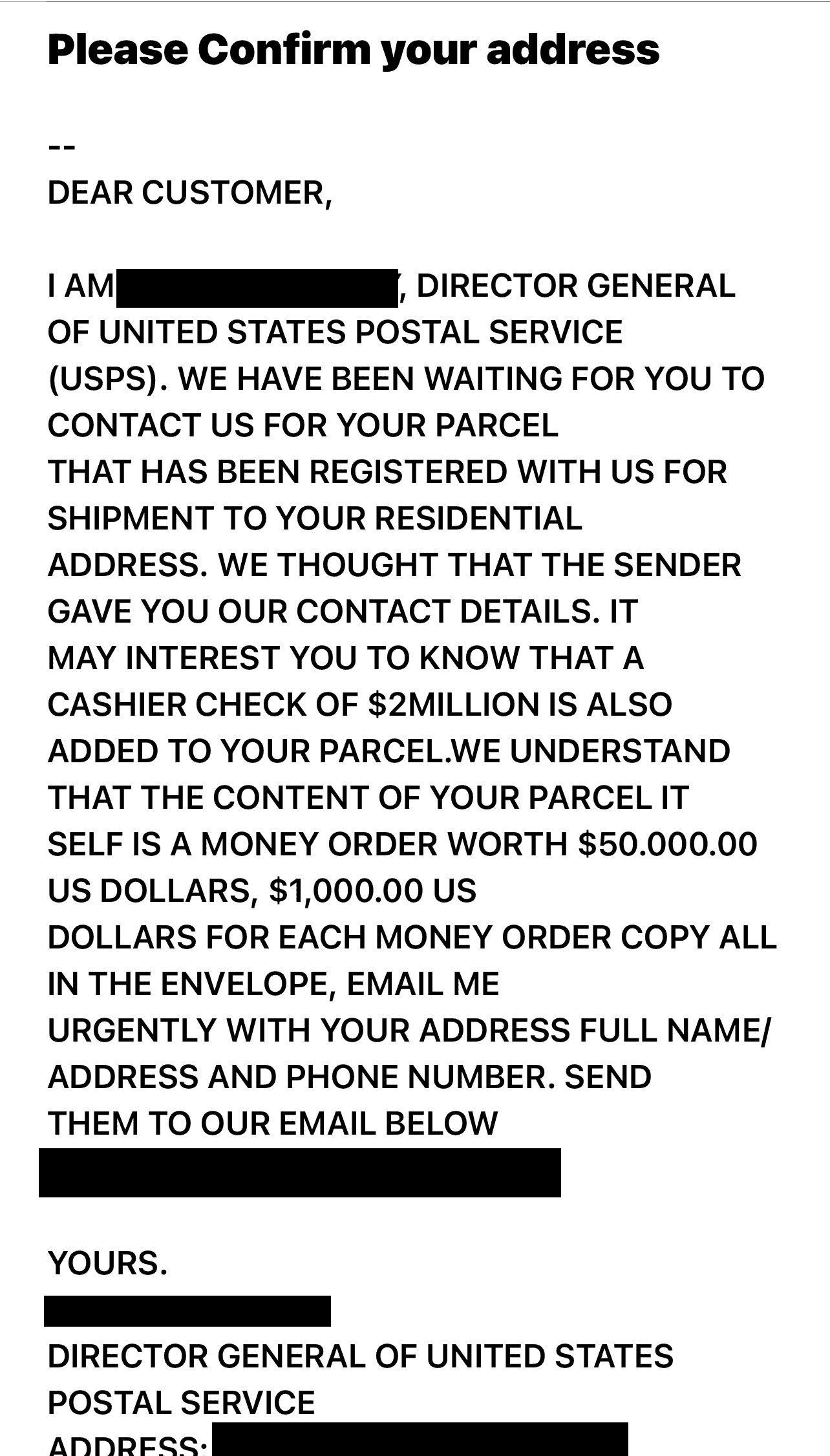
- Social engineering: The simplest way to hack an account or system? Just ask the user for their password! This may take the form of phishing or spam phone calls, so be careful who you’re giving your credentials to. Once a hacker has your password, they can easily grab your credit and debit card information, social security number, and other stuff you want to keep hidden.
- Programming-Based Hacking: More advanced than social engineering, programming-based hacking actually requires the hacker to find vulnerabilities in a system and take over all administrative privileges.
- Physical Access: Of course, possibly the easiest way to hack into a computer or system is to have physical access to it for a long time. May we implore you to be careful with your possessions or even invest in a home security system?
Why Hacking Is Bad (And Good)
Just like any power, hacking can be used for good and evil. Let’s start with the bad. Non-ethical hackers have the ability to:
- Steal credit card information, personal information, login credentials, and more
- Attack national security of other countries
- Inject malware into computers
- Modify or destroy data6
Ethical hackers, on the other hand, can use hacking for:
- Hacktivism, meaning political or social causes
- Improving security of websites or apps.
How To Protect Your Smartphone From Hacking
Whether it’s listening to a podcast on our way to work, doing quick calculations as our mental math skills have almost completely deteriorated, or putting everything from movies to doctors appointments in our calendar, there’s hardly ever a moment when we don’t have our smartphone by our side. So if we were to be hacked, we’d be in deep trouble, risking information about our credit and debit cards, location, social security number, and more.
But don’t throw away your smartphone just yet! There are a number of ways to prevent hackers from gaining access to your smartphone, and none of them require much time or effort. In just a few minutes, you can go from zero to hero regarding smartphone security. Let’s get started!
- Don’t Jailbreak: No, this isn’t a game of Monopoly. Jailbreaking your smartphone means that you have complete control over your smartphone, avoiding the manufacturer’s restrictions. So on an iPhone, for example, that means you’ll be able to use apps from places other than Apple’s official app store, plus make any tweaks to your phone’s iOS. However, we don’t recommend jailbreaking because with freedom comes lack of security. First of all, you shouldn’t be downloading apps that aren’t from the app store, as they haven’t been screened for malware. In fact, when you jailbreak your phone, you’re basically taking down all of the security measures that the manufacturer has built into their smartphones— think of it like bulldozing the fence around your house. While you might appreciate the view, you’re a lot more vulnerable than you were before. Jailbreaking also removes the smartphone’s virus protection, plus, you won’t be able to easily update your software, which could lead to further problems down the line.
- Make Smartphone Lock Sooner: In the moments where we don’t have our smartphones on hand, you might have noticed that they lock, forcing you to enter in your passcode or biometrics like your fingerprint or face. While it might be annoying to have to sign in every time, ultimately, it’s protecting your device, so we recommend setting your auto-lock to 30 seconds, meaning it will lock with no activity for 30 seconds. And if you don’t have the lock turned on at all, needless to say, you should probably change that.
- Perform All Software Updates: Companies like Google and Apple have people working around the clock to improve the smartphone’s security, so if there’s ever an iOS or Android update, do it. Although these updates can be annoying, they’re incredibly necessary for keeping up with the latest and greatest in security software. We recommend doing them at night so you’re never without your smartphone in your waking hours!
- Set up Two-Factor Authentication: If you’ve been paying attention, then you know that it’s a smart idea to turn on auto-lock so you’ll have to enter a passcode to access your smartphone, but if you want to take that a step further, we’d set up two-factor authentication. That way, if someone guesses your passcode, they still won’t be able to access your phone, as your phone company will send you another code via text or phone call. Again, this will make opening your smartphone a bit more tedious, but it’s a fantastic idea if you’re serious about avoiding hackers.
- Create Long Passcode: When choosing a passcode, people tend to do something fairly obvious, like their birthday, numbers in chronological order, or a portion of their phone number. Needless to say, this isn’t the safest practice. Rather, the numbers should be truly random, and be sure to use a six-digital passcode, the longest possible. While it will be a bit harder to remember this number, it will also be harder for hackers to guess, which is ultimately a good thing for your phone’s security. If you need help remembering your password, password vaults like NordPass and 1Password can save your passwords securely.
- Turn On Erase Data: Now, what if your smartphone is lost or stolen and for some reason, your hackers are able to access your account? Of course, this is a worst-case scenario, but in a weird way, thinking about what to do in these situations is kind of our job. Don’t worry: there is a solution, and that is to turn on Erase Data, otherwise known as setting your smartphone to self-destruct. The other option is having the phone automatically “self-destruct” after too many failed passcode attempts. Of course, this is a more extreme measure, but either will ultimately increase your smartphone’s security.
- Avoid Phishing and Pop-Ups: Phishing has gotten increasingly sophisticated, sending tech-savvy people ostensibly legitimate links and pop-up ads. While phishing is a topic we have a lot more to say about, there are some basics we want to impart to you. Don’t email any sensitive information unless you are sure of the recipient, and don’t click on any links unless you are sure they are legitimate. Scroll down to find out how you can tell if a website is safe or not.
- Turn Auto-Fill Off: Auto-fill, which fills out forms automatically with your personal and financial information, is both incredibly convenient and incredibly dangerous if your phone gets in the wrong hands. What’s to stop a hacker or thief from using your credit card information to buy themselves a new wardrobe from Supreme? While it might make your life a bit more tedious, it is the safest idea to turn off auto-fill on your smartphone.
Is This Website Safe?
Given the amount of times we use the Internet in a day, we probably spend comparatively very little time thinking about which websites are safe to use. Of course, going to a bad website can have major consequences like phishing, viruses, malware, identity theft— you name it. But how are you supposed to know when a website is unsafe, and what are some things you can do to make sure you’re only visiting legitimate websites?
If you’re short on time, here are a few quick signs of a website that’s a-okay to use:
- Padlock symbol next to URL
- HTTPS in URL rather than HTTP
- Privacy policy on website
- Website accepts all major payment methods.
Just like in dating, when you’re surfing the web, it’s important to look for red flags like:
- Browser tells you the website is unsafe
- Many pop-ups or redirects to other shady-looking websites
- Website only accepts bank transfers or wire payments
- No return policy or privacy policy on the website.
Let’s dive in a little deeper.
In-Browser Tools For Website Safety
Chances are, your browser already does a lot for you in terms of seeing which websites are safe. Personally, we use Chrome, which:
- Blocks pop-ups
- Sends “do not track” requests to websites to protect our data
- Disables unsafe flash content
- Stops malicious downloads
- Controls which sites can access our speaker, microphone, and camera
Simply go into your browser’s settings and check in the “Privacy and Security” section to see how your browser filters out the bad. Of course, these built-in browser safety tools don’t catch everything, which is why it’s important to perform other tests.
Other Website Safety Tests
If you’re not feeling confident that a website is safe, the easiest thing to do is enter it into a website checker like the Google Transparency Report7, the Norton Safe Web Checker8 or URLVoid9 pictured above. It’ll tell you whether the website is safe or not in under two seconds!
Of course, you don’t want to have to enter every website you go onto into an online checker, as that would be pretty time-consuming and inconvenient. So, there are a few things you can scan for yourself to see if a site is legit.
Use Trusted Retailers
This one may seem obvious, but especially if you’re doing any online shopping, try to use retailers who you’ve heard of, Amazon being the most obvious choice. Remember, you are giving this site your credit or debit card information along with your name, email, and address, which could be really dangerous if it got into the wrong hands.
Double Check URLs
Sometimes, scammers will misspell names of trusted URLs or replace one of the letters with a number, like writing go0gle.com instead of google.com. In a rush, this is something you can easily miss, and with fake websites imitating real websites as well as they do, it’s pretty easy to give your personal information to the bad guys. Luckily, if you use Firefox or Chrome, you can simply hover your mouse over the “anchor text” (AKA the text that is linked), to see the URL before you click on it; it’ll show up in the bottom left-hand corner of your browser. If you’re a Safari-user, just go to the view menu and click show status to get the same feature. Do a quick spell check to make sure you’re safe!
>> Related Reading: The Best Password Managers for Firefox
Note Payment Methods
Check that the website accepts all major credit and debit cards. Any normal website will have normal payment methods from the major credit/debit card companies, like Mastercard, Visa, American Express— you get the drill. If a website only accepts bank transfers or wire payments, steer clear.
Check Review Sites
The Internet is the perfect place for people to air out their problems to as many people who will listen. Chances are, if there’s a subject, people have reviewed it on the web, from restaurants to e-commerce sites. Take advantage of people’s insatiable need to publicly rate everything and check review sites like TrustPilot, especially if it’s an e-commerce site. You don’t even necessarily have to use a review site. Simply ask Google if the website/ company is a scam and see what people have said. If multiple people say it’s a scam, they are most likely correct.
Check For HTTPS
Now, this isn’t 100% foolproof, but most reputable websites will have URLs that begin with HTTPS rather than HTTP; and yes, if you’re wondering, the S does stand for secure. Basically, that tiny little letter is the difference between a secure website that encrypts your data and a scam website that steals it (with exceptions, of course). If the website is secure, you’ll see a padlock to the left of the URL, but note that some unsafe websites have HTTPS, so it’s not guaranteed to be safe. However, one hard and fast rule that you can follow is never enter your password or financial information on any website missing the padlock.
Look For A Privacy Policy
The truth is, most reputable websites have privacy policies, as many countries require them by law, so be sure to look for one on a website. Now, we’re not saying you’ll be able to understand these policies, as they’re often written in what we in the industry call “legalese”. But to get a good idea of how the website will use your data, press Control F and search for things like “third-party,”, “data,” “store,” and “retain”. If a website lacks a privacy policy at all, we wouldn’t trust it.
Don’t Blindly Trust “Trust” Badges
Do you know how easy it is to get one of these so-called “trust badges” on your website? It’s so easy that you can literally type in “trust badges” to Google images and drag them onto your site. Although these seals may look legitimate, literally anyone could add them to their website, from huge companies like Barnes & Noble to the shadiest “foreign prince” on the web. We’re not saying these trust badges automatically make a site untrustworthy; however, you shouldn’t mistake them for security.
Look For These Red Flags
There are a number of red flags that not only make a website a poor user experience, but also might be a clue that something is amiss. Watch out for:
- Flash warnings
- Pop-ups
- Too many exclamation points!!!!!
- Redirects to other sites that look unsafe
- Search engine warnings from your browser or search engine
- Bad spelling and grammar
- Illogical text
- Weird pictures
- No space to leave product reviews
- No return policy or privacy policy on site
- Prices that are too good to be true.
As much as we hate to judge a book by its cover, these are all signs of a website that’s not super safe.
Look Up Domain Owner
Most reputable websites, particularly for businesses, will have a domain owner, easily lookup-able on ICANN’s Domain Name Registration Data Lookup10. This website will also tell you the date this registry expires, the organization and mailing address of the registrant, and the data the registry was created.
Call Company
We know it sounds old-fashioned, but even the most advanced robots have trouble mimicking humans exactly. Therefore, if you’re not sure if a website is from a real company, an easy way to find out is simply by calling them over the phone! Typically, most websites will provide a phone number either on their Contact or About Us pages. If you can’t find it, you can also try looking it up on the exact same whois lookup above, or try contacting them through customer support.
Additional Web Security Tools
Finally, a straightforward way to avoid going to harmful websites is to use web security tools that protect you from viruses. Here are some top examples:
With these software programs downloaded, you won’t have to worry about giving your personal data to unsafe sites. It will do the work for you so you don’t have to worry about it at all!
VPNs
VPNs are Virtual Private Networks that encrypt your web traffic in a tunnel, completely hiding your web activity and replacing your IP address. They’re especially useful if you’re on a public network like a coffee shop, or if you simply want to access another country’s server so you can enjoy Netflix Italy. VPNs make it much less likely that your device will be hacked, and you can easily download them onto your phone, tablet, computer, or even your router.
Our Experts’ Favorite VPNs: ExpressVPN review, NordVPN review, CyberGhost review, Surfshark review
Product Spotlight: ExpressVPN

Perhaps the most recognizable VPN on the market, ExpressVPN has over 2,000 servers in 148 locations, so it’s very likely you can find one near you. Based in the British Virgin Islands, ExpressVPN isn’t subject to any international surveillance alliances, so your data is safe with them. With ExpressVPN, you’ll be able to torrent files through uTorrent, access private and public networks simultaneously through split tunneling, and even access Netflix, to all the cinephiles out there. Plans are available on a monthly, six-month, or yearly basis.
| Term Length | Monthly Price | Billing |
|---|---|---|
| 1 month | $12.95 | Billed $12.95 monthly |
| 6 months | $9.99 | Billed $59.95 every 6 months |
| 12 months | $8.32 | Billed $99.95 every 12 months |
Identity Monitoring Services
Having your identity stolen can be one of the most emotionally and financially draining things you can go through, which is why it’s important to employ an identity monitoring service. While none of them are guaranteed to completely prevent identity theft, they can monitor key areas that could indicate that your credentials have been stolen, such as your credit reports, bank, credit card, and investment accounts, as well as the dark web and other criminal activity areas. For example, if your name shows up on a sex offender registry, you’d want to know about it, right? The same goes for if a new tax return is filed in your name. Plus, if your identity is stolen, most identity monitoring services will reimburse you for your losses for up to a million dollars. Not too shabby!
Top Identity Monitoring Services reviews from our Experts: LifeLock review, Identity Guard review, IdentityForce review, Aura review
Product Spotlight: PrivacyGuard

PrivacyGuard will monitor your credit reports monthly from the three main credit-reporting bureaus, Experian, TransUnion, and Equifax, along with your financial account, the dark web, public records, neighborhood reports, registered offender locators, and more. Say there was a neighborhood report that included your name. You’d be alerted via email and SMS alerts, and if your identity is stolen, you could be reimbursed for up to a million dollars. To try PrivacyGuard out for 14 days only costs a dollar!
| Credit Protection | Identity Protection | Total Protection | |
|---|---|---|---|
| Monitoring of 3 Credit Bureaus | Yes | No | Yes |
| Credit Score Alert Frequency | Yes | No | Yes |
| 24/7 Triple-Bureau Daily Credit Monitoring | Yes | No | Yes |
| Public and Dark Web Scanning | No | Yes | Yes |
| Social Security Number Monitoring | No | Yes | Yes |
| Driver’s License and Passport Monitoring | No | Yes | Yes |
| Bank Account Monitoring | No | Yes | Yes |
| Debit and Credit Card Monitoring | No | Yes | Yes |
| USPS Address Change Verification | No | Yes | Yes |
| Email, Phone, Name, DOB Monitoring | No | Yes | Yes |
| ID/ Application Verification Monitoring | No | Yes | Yes |
| Public Records Monitoring | No | Yes | Yes |
| Children’s Social Security Number Monitoring | No | No | Yes |
| Email and Text Alerts | Yes | Yes | Yes |
| Dedicated ID Fraud Resolution Agent | Yes | Yes | Yes |
| Online Fraud Assistance | No | Yes | Yes |
| $1 Million ID Theft Insurance | No | Yes | Yes |
| Lost and Stolen Wallet Protection | No | Yes | Yes |
| Annual Public Records Report | No | Yes | Yes |
| Reduced Pre-Approved Credit Card Offers | No | No | Yes |
| Neighborhood Reports | No | No | Yes |
| Registered Offender Locator | No | No | Yes |
| Emergency Travel Assistance | No | No | Yes |
| Medical Records Reimbursement | No | No | Yes |
| Monthly Price | $19.99 | $9.99 | $24.99 |
Password Managers
One of the most annoying things about technology is having to remember so many different passwords for different accounts. Plus, each account probably has its own rules, like you must have special characters, you can’t have numbers, no repeated letters, and more, making it even harder to remember everything. And the process of resetting your password is less than fun, especially because you’re probably just going to forget it again!
Password managers make it easy to access your accounts by remembering your passwords for you, in a secure fashion of course. They’re also great for storing important or sensitive information, and even automatically filling out web forms for you!
Best Password Managers According To Our Experts: Dashlane, Keeper, NordPass, Password Boss, LastPass, 1Password
>> Related Reading: Best Password Managers of 2025
Product Spotlight: Keeper
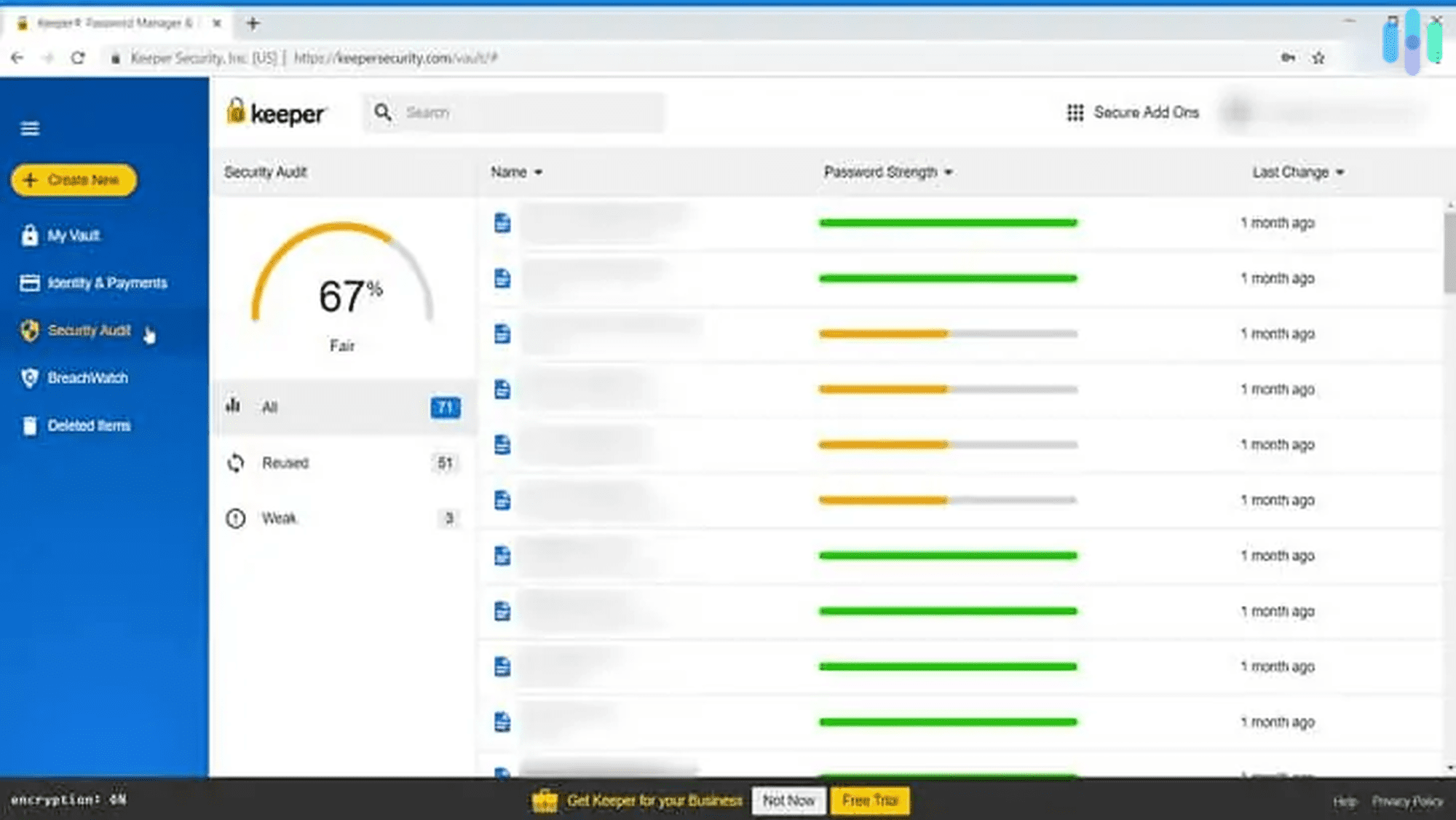
There are a few things more annoying than having to reset your password, but with Keeper, that’ll never happen again. Keeper remembered all of our passwords across all of our devices. To sign in to an account, all we had to do was use fingerprint ID on our iPhones and iPads, and enter a code sent to our mobile device while using our computer. Keeper also made sure that all of our passwords were strong in the first place with a password strength report. After identifying which of our passwords were weak, old, or repeated, Keeper generated strong new passwords for us via their password generator. They even filled in forms for us using KeeperFill, which certainly upped the convenience factor even more. And don’t worry; all of our passwords were stored in an encrypted vault for safekeeping.
| Individual | Family | |
|---|---|---|
| Number of Private Vaults | 1 | 5 |
| Unlimited Password Storage | Yes | Yes |
| Unlimited Identity/ Payments | Yes | Yes |
| Fingerprint and Face ID Login | Yes | Yes |
| Unlimited Devices and Sync | Yes | Yes |
| Secure Record Sharing | Yes | Yes |
| Emergency Access | Yes | Yes |
| Web App | Yes | Yes |
| 24/7 Support | Yes | Yes |
| 10 GB Secure File Storage | No | Yes |
| Monthly Price | $2.50 | $5 |
| Yearly Price | $29.99 | $59.99 |
Recap
Being online doesn’t have to be scary. There are many tools out there that can protect you online, like VPNs, password managers, identity monitoring services, and simply adjusting the settings on your devices. Knowing how to surf online safely is the first step to protecting your personal credentials, and with guides from Security.org, we’ll do our best to keep you safe and secure. Be sure to check out our guides to the best VPNs and the best identity monitoring services, all of which have been tried and tested by our experts.