VPNs are an increasingly popular way to connect to the internet. They are often described as tunnels between your computer and servers that hide your internet activity from prying eyes. But is that really true, and just how safe is a VPN? For instance, does a VPN use encryption methods so your data is completely encoded and safe from hackers?
Our experts have tested over 50 different VPN providers so we can confidently say that VPNs do encrypt your data. But, not all encryption is the same. We’re going to break down everything you need to know about VPN encryption to ensure the VPN you choose gives you the protection you need. Let’s dive right in!
Do VPNs Use Encryption?
VPNs, or virtual private networks, are services that enhance your online privacy, and they do that by creating an encrypted network just for you. So yes, all VPNs use encryption. Some VPNs, however, use more secure types of encryption, such as 256-bit AES. That’s the highest level of encryption used by the best VPNs, such as NordVPN, Surfshark, and Private Internet Access (see those below!).
Are VPNs and Encryption One and The Same?
VPN and encryption are two different things, though; they’re not one and the same. The main difference between a VPN and encryption is that a VPN is a service that utilizes encryption, among other things, to shield your internet activity from privacy breaches. On the other hand, encryption is just one process that encodes data to make it unreadable to anyone without an encryption key.
Still confused? Okay, let’s simplify. A VPN can be likened to the measures you use to secure your home. That might include a security system, locks and bolts, or even a guard dog. All those measures make up your home security, in the same manner that encryption, private tunnels, and VPN protocols make up your VPN. Encryption is just one part of your VPN, which we can liken to your door lock.
If that’s clear enough, let’s move on.
Why Do You Need a VPN Service?
As our own research into consumer usage reveals, a VPN can be handy for a number of reasons.
Privacy
Probably the most straightforward reason people use VPNs is to protect their privacy. By encrypting your web activity and IP addresses, a VPN ensures that no one who intercepts your internet signal can decode that data. This makes VPNs especially useful when you’re logging on to a public Wi-Fi network at your local coffee shop or the public library. A VPN prevents others on the same network from spying on what you’re doing. This is also where VPNs are more effective for privacy than using a proxy server, which only hides a user’s IP address, but not all web activity.
But privacy can also be important to someone at home who is using a private router to access the internet. Most users use a commercial internet service provider (ISP) to get onto the internet. And in most cases, an ISP provides plenty of protection from hackers. An ISP doesn’t, however, provide protection from government spying. Users who spend time on the dark web or torrenting sites may prefer to be hidden from the government and even their own ISP. A VPN provides that kind of protection.
Bypassing Government Restrictions
Many countries restrict internet access or ban certain sites for ideological reasons. A VPN allows citizens to bypass internet restrictions and use the internet freely, without censorship. Some of these countries that restrict internet access also outlaw the use of VPNs. So, make sure to check your local regulations to avoid any legal trouble. Check out our guide to the legality of VPNs for more details.
Bypassing Streaming Restrictions
Most of us use a streaming service to watch television shows and movies. Not everyone knows, however, that content can vary based on a user’s geographic location. Netflix and Amazon Prime, for instance, both offer content in Canada that can’t be seen just across the border in the U.S. And YouTube TV provides content based on a user’s location within the U.S., so Chicago viewers get different local channels from Atlanta viewers.
Because they hide your IP address, a Netflix VPN, a Prime Video VPN, and a YouTube TV VPN all prevent those streaming services from seeing your geographic location, which means you can access content from anywhere in the world. We love romance movies ourselves, so we use a Netflix VPN to access the Netflix catalog in France. Let’s face it, France knows how to do romance right. We also use a VPN when we’re abroad to access U.S. content with a U.S. IP address. For more information, check out our complete guide to the best VPNs for streaming.
Preventing Throttling
VPNs help with streaming in another sense as well. Some ISPs throttle internet signals once users have reached a data maximum each month. This slows down streaming, which makes watching your favorite show difficult if not impossible. However, by encrypting your internet connection, a VPN prevents ISPs from knowing how much data you are using, meaning that you can binge-watch Game of Thrones with zero stress.
FYI: The United States restored net neutrality in April 2024 which means ISPs can no longer throttle specific websites. But, they can still throttle your internet speeds for a variety of other reasons like data caps or infrastructure issues. VPNs help you get around these types of throttling, too.
Identity Protection
Finally, some users employ VPNs simply for the extra protection it adds from hackers. As we’ve already mentioned, a VPN’s primary job is to encrypt your information, particularly your PII (personal identifiable information) so it can’t be stolen in transit. PII includes your:
- Birthdate
- Social Security number
- Mother’s maiden name
- Place of birth
- Biometric information
In short, PII is anything that could be used to track and clone your identity.1 When a VPN encrypts your PII, however, even if a thief could get their grubby hands on it, they wouldn’t be able to read it. Find out more about how to prevent identity theft in our complete guide to identity theft protection.
How Does a VPN Work?
To enable stress-free streaming, anonymity, and security, here are the two major ways VPNs work:
- VPNs conceal your IP address by redirecting your internet signal through a remote host that assigns it a new IP address. This means you can browse the web with complete anonymity.
- VPNs encrypt all the data you send and receive, including your browsing activity, so that no one can read it but you. This not only protects your personal data, but it further conceals your identity.
>> Related Reading: Five Easy Opt-Outs to Protect Your Identity and Privacy
Types of VPNs
There are three different kinds of VPNs:
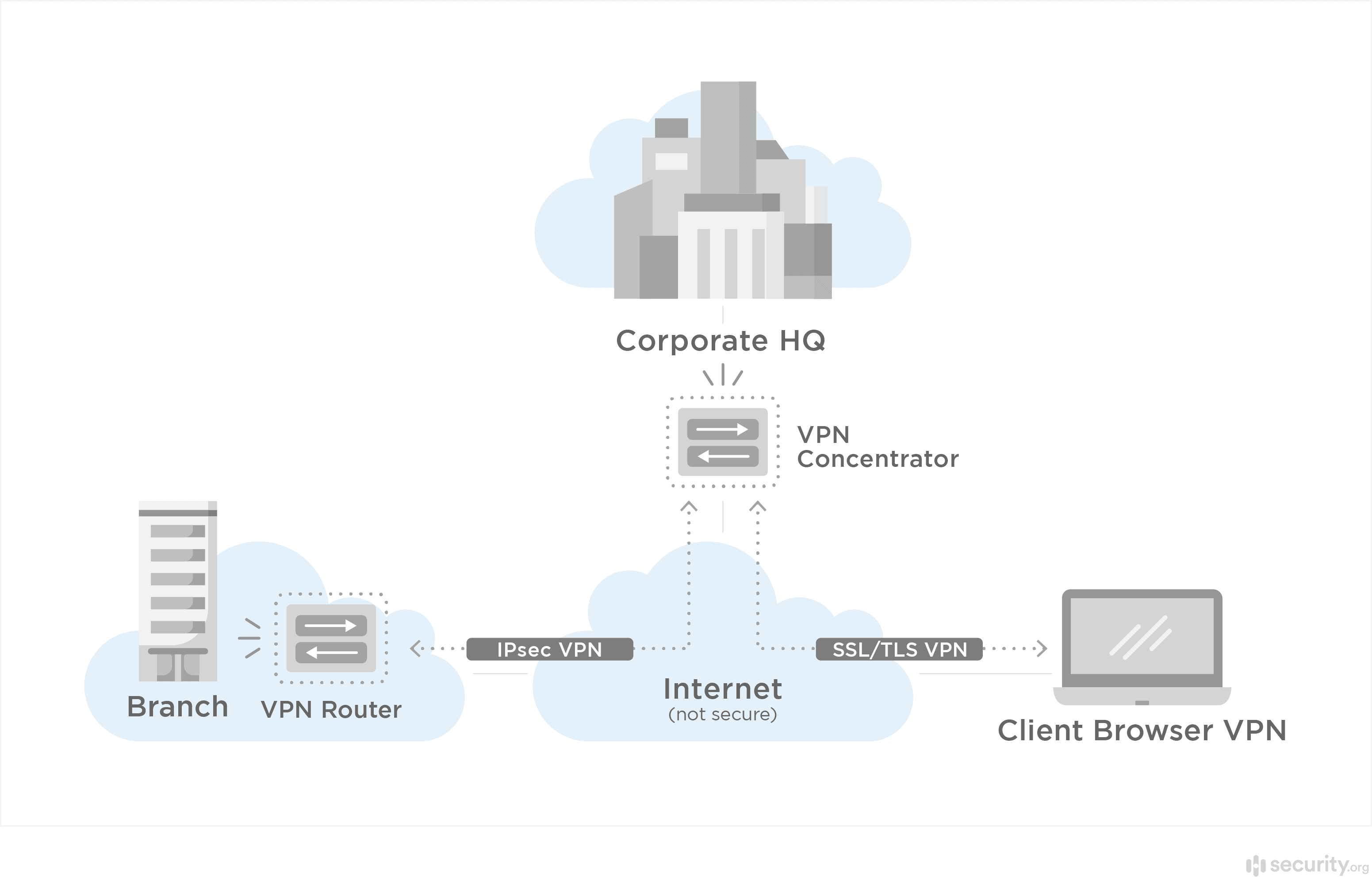
- Remote access: Remote access VPNs are the most common type of VPN. They involve connecting a computer to a “remote” server. That server provides the encryption that protects your data when you’re online.
- Intranet site-to-site access: A site-to-site access VPN creates a kind of floating tunnel between multiple computers networked together. Frequently used in business, these VPNs allow employees working in different parts of the world to connect to one another over a single encrypted network. An intranet VPN encrypts the tunnel but allows the various computers in the network to communicate directly without encryption.
- Extranet site-to-site access: In contrast to an intranet site-to-site VPN, an extranet VPN creates a tunnel between two separate intranets. The most common example is two separate companies collaborating on a project. Each company’s intranet connection allows users within it to communicate with each other directly. The extranet connection keeps both companies’ intranets safe while allowing their users to communicate.
How a VPN Protects Your IP Address and Privacy
Once you log on to a VPN — that is, once you enter the encryption tunnel — the VPN hides your data from anyone who might want to see it. In the simplest terms, what you do online when you are connected to a VPN is completely private. One of the advantages of a VPN is that the privacy extends to your IP address, the identifying information of your device that lets others know your location. When you log in to a VPN, you can connect to a server in a number of locations around the world. In addition, the VPN issues you an IP address that conceals your actual IP address. The end result? You are absolutely anonymous.

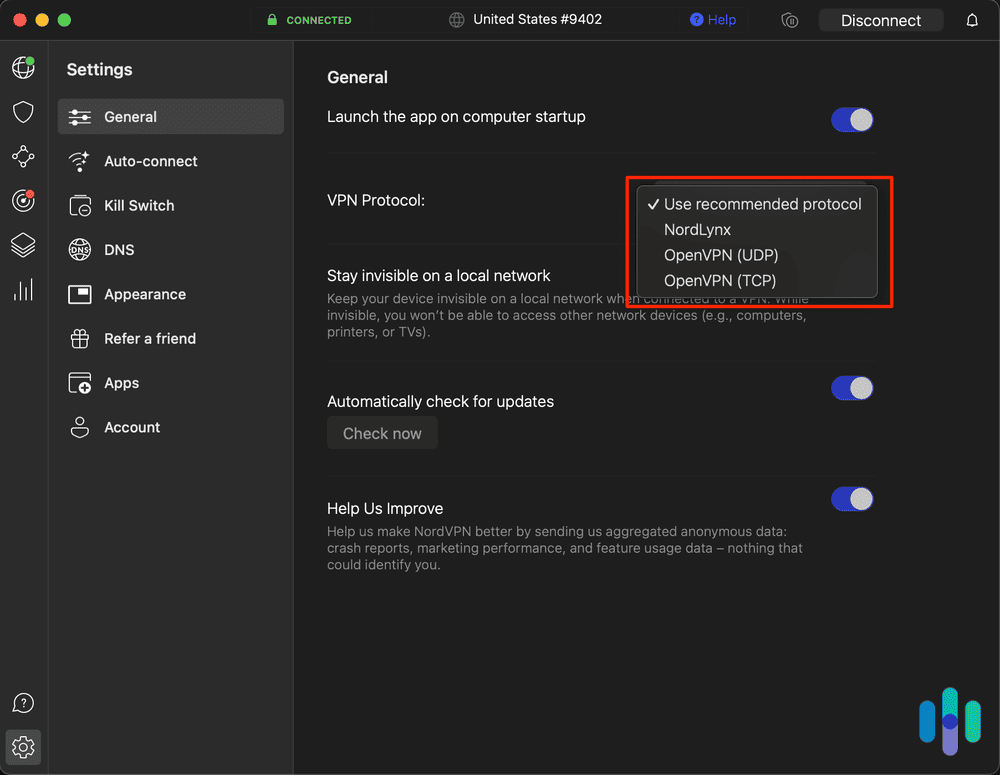
What Encryption Methods Do VPNs Use?
You can think of a VPN’s encryption as a set of tools, each one providing its own layer of protection. VPNs use several encryption methods:
- Symmetric encryption: Symmetric encryption is a simple concept that dates back to Roman times and the Caesar cipher. It means one person uses an algorithm to encrypt the message they send to someone else. Both the sender and the receiver know that algorithm. In other words, the relationship to the code is symmetric. Anyone without access to the algorithm, on the other hand, has no means to decode the message.
- AES encryption: Of course, the algorithms or “ciphers” used in contemporary computing go well beyond anything the Romans might have dreamed up. One of the most commonly used ciphers today is AES, the Advanced Encryption Standard. The U.S. military developed this method.2 It involves dividing texts into grids and then scrambling those grids. AES divides data streams into 128-bit chains of cipher blocks. The “key” to decipher these chains can be 128, 192, or 256 bits long, each progressively harder to break. The best VPNs typically use AES-256 to encrypt user data.
- Public-key encryption: Symmetric encryption has one flaw — in order for the two sides to understand one another, they must share the cipher key. When one side sends this key to the other, it is vulnerable to interception by hackers. Once a hacker has the key, the encryption is useless. Public-key encryption addresses this problem by creating separate encryption and decryption keys. The VPN server encrypts data using a public key, but when that data reaches the user’s computer, the user has their own private key for decrypting the data.
- Transport layer security: Finally, transport layer security, or TLS, provides a system of authentication between servers and users, ensuring that a hacker can’t pretend to be on one side or the other in order to steal the cipher. A VPN server enacts transport layer security when a user first connects to the server as a means of verifying identity before encryption can begin.
What Protocols Can a VPN Employ?
Essentially, internet protocols are sets of instructions for how a given VPN transmits data across a network. There are several different protocols, each with its own pros and cons.
OpenVPN
Pros
- OpenVPN is open-source software. This means it is free to use.
- Anyone can test out OpenVPN or suggest bug fixes. In fact, an entire internet community regularly tests OpenVPN, ensuring it features the most secure set of protocols.
- No single company controls OpenVPN. This means it is free of potential backdoors, hidden places in the program a company or government agency can use to spy on users’ activities.
Cons
- Because it utilizes so many different encryption layers, OpenVPN is not as fast as other protocols.
PPTP
Pros
- PPTP is among the fastest VPN protocols, useful for those who are looking for speed but don’t need a lot of security.
Cons
- PPTP is one of the oldest protocols,3 so it is a well-known entity to hackers. In short, it cannot protect against a serious hacking attack.
L2TP/IPsec
Pros
- The L2TP protocol is based on PPTP, so it is faster than most other protocols.
- It is, however, more secure than PPTP because it double-encapsulates data.
Cons
- L2TP can’t work on its own; it must be used in conjunction with IPsec.
- Because it uses UDP, L2TP is easy for sites to block.4
SSTP
Pros
- SSTP uses AES encryption for enhanced security.
- The protocol gets past blocked sites by using SSL and Port 443 (a port that secure websites use) so that it looks like normal HTTPS web traffic.5
Cons
- Microsoft created SSTP, which means it could include backdoors, or methods by which Microsoft and government agencies could spy on activity within the VPN.
IKEv2
Pros
- IKEv2 is faster than OpenVPN.
- It can also employ AES encryption.
Cons
- This protocol is difficult to set up on the server end, so inexperienced VPN companies might make mistakes.
- Firewalls can block it.
WireGuard
Pros
- Developers created WireGuard to be a faster alternative to OpenVPN.
- Like OpenVPN, the protocol employs open-source software, so anyone can test it.
Cons
- WireGuard has only been in use for two years, so the open-source community hasn’t had a lot of time to rigorously test it.6
What’s Wrong With Public Networks?
Don’t get us wrong; we’re grateful for public Wi-Fi at our favorite restaurants, since they allow us to get fast, free signals on the go. However, “public” means everyone in the vicinity shares the same internet connection. Even a relatively unsophisticated hacker can look over your digital shoulder if you’re sharing an internet connection. By putting you into an encrypted tunnel, a VPN makes sure that can’t happen.
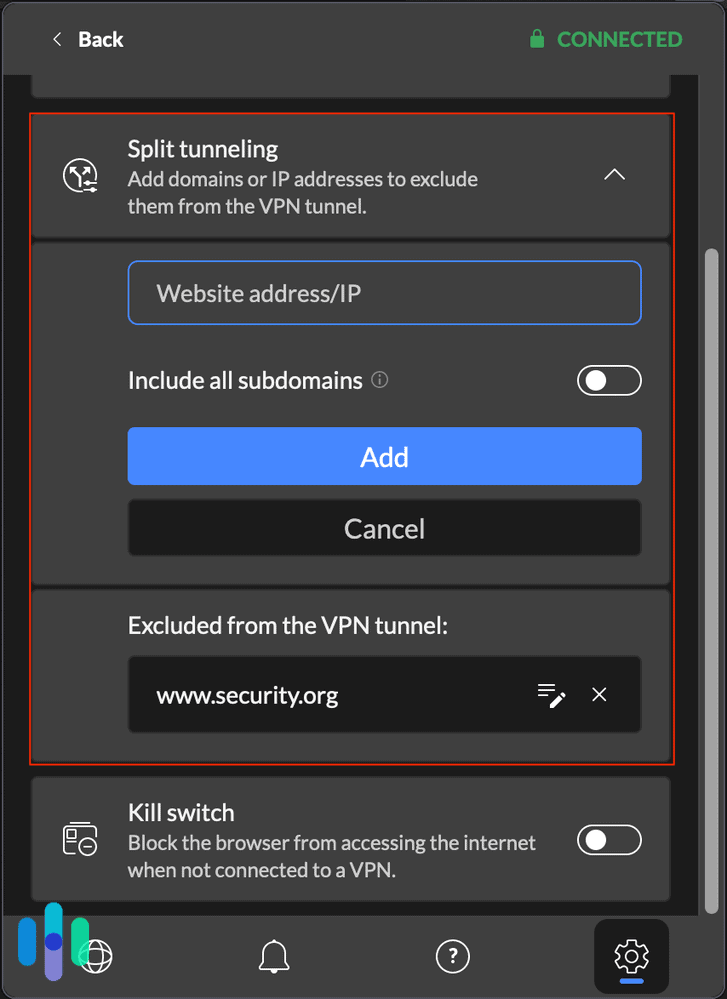
FYI: Many VPNs offer a feature known as split tunneling. With split tunneling, you can maintain a public Wi-Fi connection at the same time you connect to a VPN. You could stream content for free on one server while you protect sensitive data on the other.
Does a VPN Make Online Users Anonymous?
One of the chief reasons to use a VPN is that it makes you anonymous online. When you connect through an ISP, the ISP assigns you a specific IP address that allows hackers and government agencies to track your online behavior. That same IP address allows streaming content providers to know exactly where you are and ISPs to know which websites you’re visiting and how much data you’re using. A VPN encrypts your data so no one can see what you’re doing, but it also assigns you an IP address that isn’t linked to your device. This means wherever you go and whatever you do online is completely private and anonymous.
» Learn more: A Static vs Dynamic IP Address
How to Choose a VPN Service
We’ve already discussed many of the elements you should look for when choosing a VPN. Here’s a more complete list of features to consider:
-
- Split tunneling: This feature allows you to log on to the regular internet at the same time you log on to a VPN. Sometimes, split tunneling can even save you money if your VPN has data limits. You can use public Wi-Fi to stream your music and share your work files securely.
-
- Multi-hop technology: “Multi-hop” means the VPN routes your data through at least two different servers. That makes it harder to follow, as it encrypts your data multiple times.
- Streaming support: Some VPNs are configured to access streaming services. Others get blocked. Look for VPNs that work well with the streaming services you prefer.
- Torrenting support: Any VPN that conceals your IP address and encrypts your data will allow you to torrent in anonymity. However, not all VPNs work with torrenting sites, so if that’s something you’re interested in, check out a torrenting-compatible VPN.
- Kill switch: At a minimum, you should look for VPNs that have kill switches. Kill switches automatically shut down your web browsers and apps if your VPN connection is lost.
- Privacy policy: Always check a VPN’s privacy policy. A privacy policy tells you what the VPN does and doesn’t log. All VPNs log some information, if only for billing purposes. However, the best VPNs don’t log IP addresses, browsing activities, or timestamps of connections.
- Location: Where a company is headquartered plays an important part in their ability to protect your privacy. For example, the U.S. government can subpoena companies located in Five Eyes, Nine Eyes, or 14 Eyes countries and force them to turn over customer data.
- Encryption tools and protocols: As we discussed above, different VPNs use different protocols and encryption tools to keep you safe and anonymous. We generally prefer those that use AES-256 encryption and OpenVPN protocols.
- Speeds: There are three important speeds to consider when choosing a VPN: upload speeds, download speeds, and ping (latency) speeds. Every VPN slows your computer down to some extent. However, your computer’s speeds with the VPN running compared to the speeds without it running can give you a good indication of whether it will be fast enough for what you do online.
- Price: Obviously, prices and pricing structures vary widely among VPNs. Many companies, for instance, offer deep discounts if you’re willing to sign up for a long-term contract. You should always carefully consider just what you’re getting for the money. Here are some questions to answer in your research:
- How many simultaneous connections do you get?
- How many devices can you connect overall?
- Are there any data usage limits?
Obviously, we prefer to get as many features as possible, and we generally like services priced under $10 a month. You can check out all these features for each individual VPN, or visit our list of the best VPNs to see side-by-side comparisons.
Recap
VPNs are definitely encrypted. That’s one reason for their popularity: They allow users to surf the web safely and anonymously. Of course, VPNs are not all created equal. They use different encryption methods such as public-key encryption, transport layer security, and AES. They also combine these methods with several different protocols, like OpenVPN, SSTP, and WireGuard. They also come with a number of different features, from split tunneling to multi-hop technology. Ultimately, we recommend using VPNs in general, but we also suggest taking your time to consider all the options before deciding on one.
FAQs
Before you leave, check out our answers to some of the most frequently asked questions about VPN encryption.